Visualize and defend against identity threats
Unmask identity risks. Secure your enterprise.
See identity threats in real-time and shut down cyber risk with adaptive identity built for today’s enterprise.
Challenge & solution
Hidden threats in a complex world
Every identity is a potential entry point for a security breach. In today's interconnected environment, seeing who has access to what—and whether that access is risky—has become a significant challenge. Without clear visibility, threats can go undetected until it's too late. Organizations need a way to move from a reactive security posture to a proactive and adaptive one, identifying and neutralizing threats before they can cause damage.
See and secure every identity
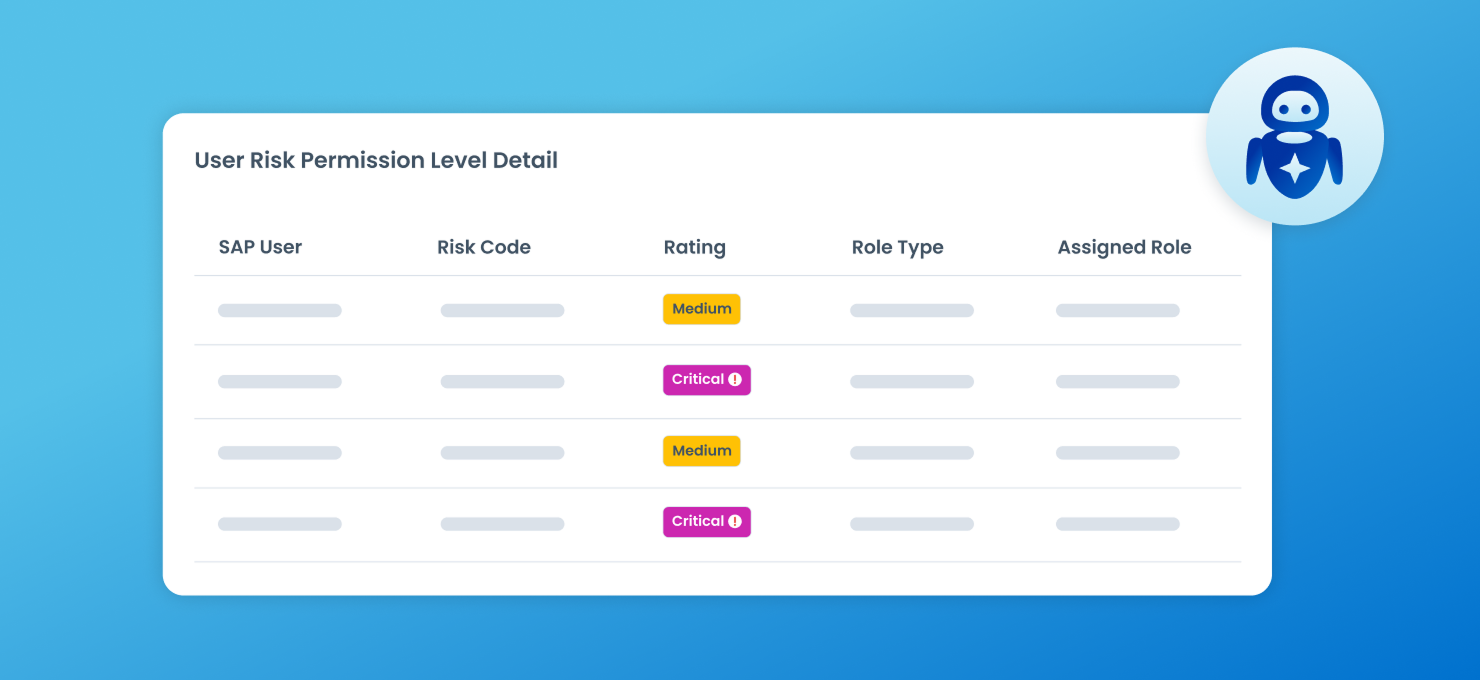
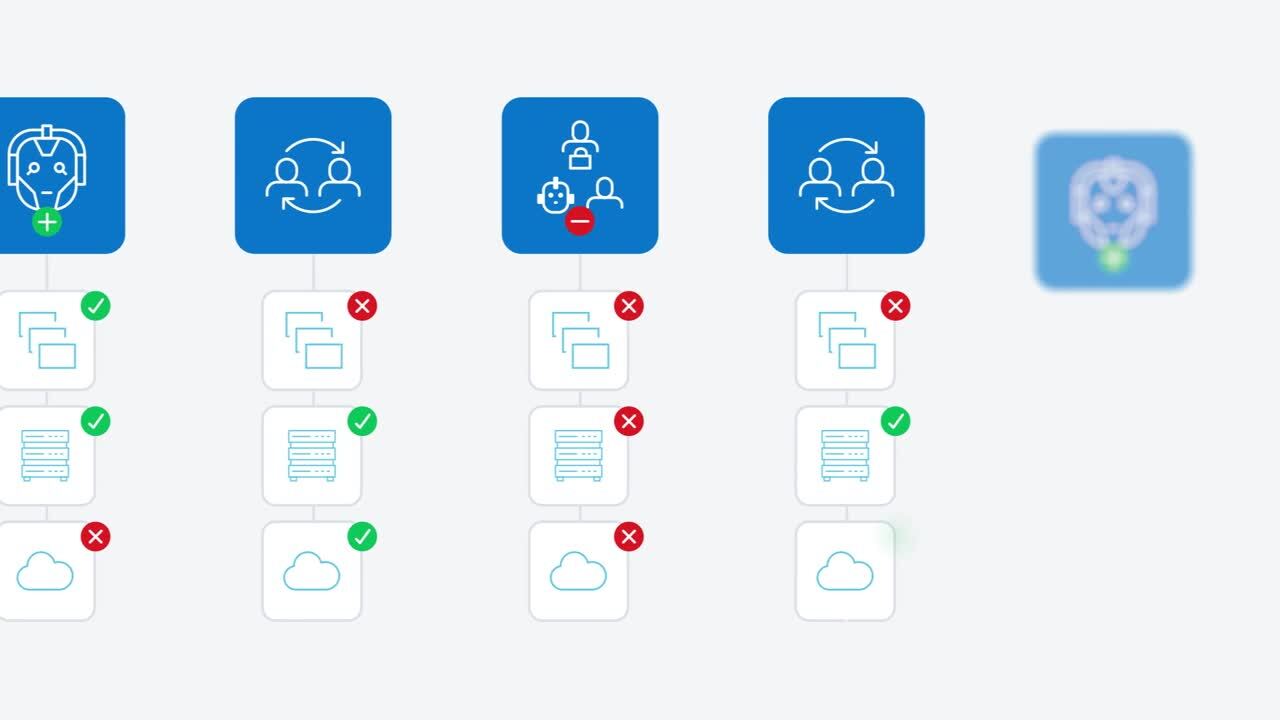
Gain a single, comprehensive view of all identities—human, machine, and AI agents—and their access.
Use AI to automatically detect risky users, unusual access patterns, and inappropriate access privileges.
Enforce least privilege access consistently across your entire digital ecosystem.
Automate responses to policy violations to reduce your window of exposure.
Act swiftly, remediate vulnerabilities, and protect your most critical assets with confidence.
Continuously monitor access to adapt to new and evolving threats.
Results
Unified identity security. Real business results
Faster to detect and respond to attacks using AI
Saved by preventing ransomware payment through robust identity security
Access certification time dropped from 1 year
Time to deprovision user access, down from 30+ days
Benefits
Gain clarity, control, and confidence
When you have full visibility into every identity and their access, you’re empowered to identify and address threats with confidence. SailPoint gives you the tools and intelligence to protect what matters most—so you can reduce risk, streamline your defenses, and move forward with greater clarity and control.

Stay ahead of risks with real-time visibility
Discover, manage, and secure access for every identity. Gain a complete picture of your environment to proactively defend against threats targeting employees, non-employees, even machine identities and AI agents.
Key offerings
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
Customer Stories
Trusted by leading organizations
Businesses across industries rely on SailPoint to safeguard identities, strengthen security, and stay ahead of evolving threats.
Related resources
Learn how to visualize and defend against identity threats
faq
Answers for your identity threats
What SailPoint solutions help with mitigating cyber risk and defending against identity threats?
SailPoint offers solutions like SailPoint Identity Security Cloud, AI-driven analytics, and automated access controls. Together, these tools provide clear visibility, detect potential risks, and automate responses to strengthen your overall security posture.
How does identity security help in visualizing threats?
Identity security provides a centralized view of all user access rights across your entire IT environment. This comprehensive visibility allows you to see who has access to what, identify permissions that are excessive or unused, and spot patterns that may indicate a threat. Without this clarity, risky access often remains hidden. In additional SailPoint Observability and Insights provides deep visibility and context into every identity and access path with an interactive identity graph.
What kind of identity threats can be detected?
You can detect a wide range of threats, including excessive permissions that violate the principle of least privilege, orphaned accounts left active after an employee has departed, dormant accounts that could be hijacked, and toxic combinations of access that create separation-of-duty conflicts. AI can also help identify unusual access patterns that deviate from normal behavior.
How does automation help in defending against threats?
Automation enables you to respond to threats at machine speed. When a risk is identified, automated workflows can trigger alerts, initiate access reviews, or automatically revoke inappropriate permissions. This minimizes the time an attacker has to exploit a vulnerability and reduces the manual workload on your security teams.
Can I manage both my human and non-human identities in one place?
Yes. SailPoint Identity Security Cloud governs human, non-employee, machine, and agent identities within one unified experience. This enables consistent policy enforcement, streamlined access certifications, a complete view of access risk across your entire organization for humans and machines alike, and allows for complete lifecycle control through a single governance platform. This unified approach reduces complexity, closes security gaps, and simplifies compliance across all identity types.
Contact us
Adaptive identity: The foundation of enterprise security and trust
Give your teams the clarity and confidence that comes from a strong identity security foundation. See threats sooner, respond faster, and empower your people to do bold, innovative work.