Operationalize zero trust for scalability
Reduce risk, build trust, scale securely
Move beyond theory with an identity-centric approach that automates least privilege and verifies access at enterprise scale.
Challenge & solution
The reality of zero trust at scale
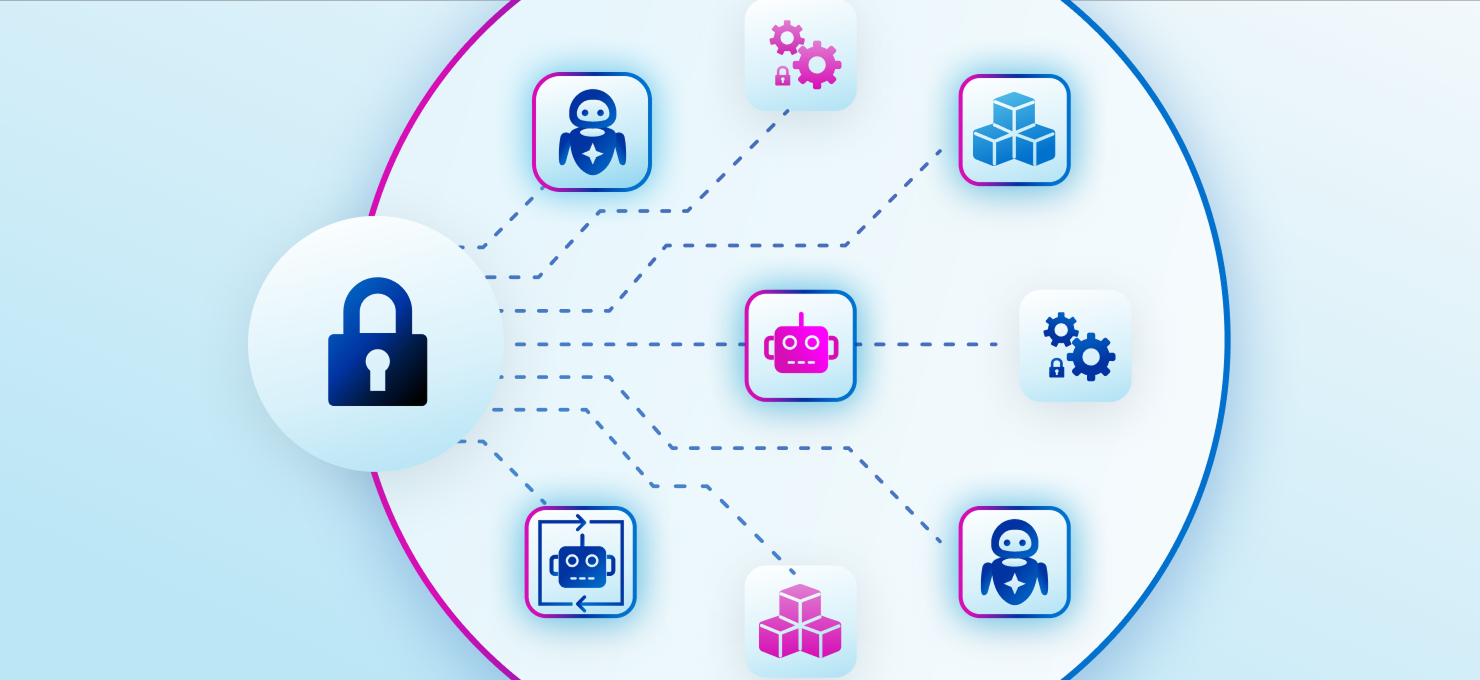
Zero trust is essential but implementing it across a complex enterprise is difficult. When you have thousands of human, machine, and AI agent identities accessing hybrid environments, manual verification fails. You cannot rely on static policies in a dynamic world. Organizations need a way to enforce "never trust, always verify" without creating friction or slowing down the business.
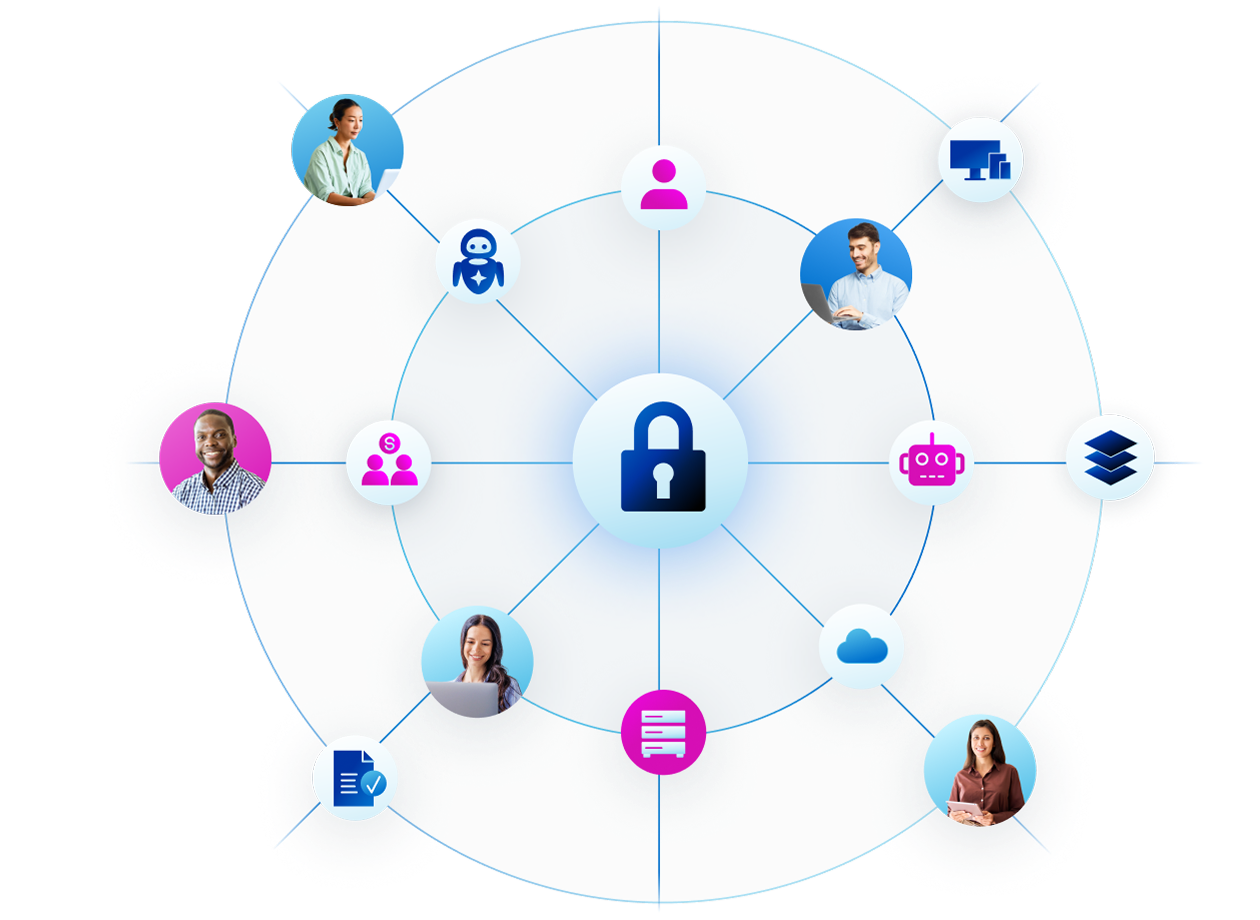
Identity is the foundation of zero trust
Enforce least privilege dynamically based on user roles and real-time risk.
Extend verification to every identity type: employees, contractors, bots, and AI agents.
Automate provisioning and deprovisioning to close security gaps instantly.
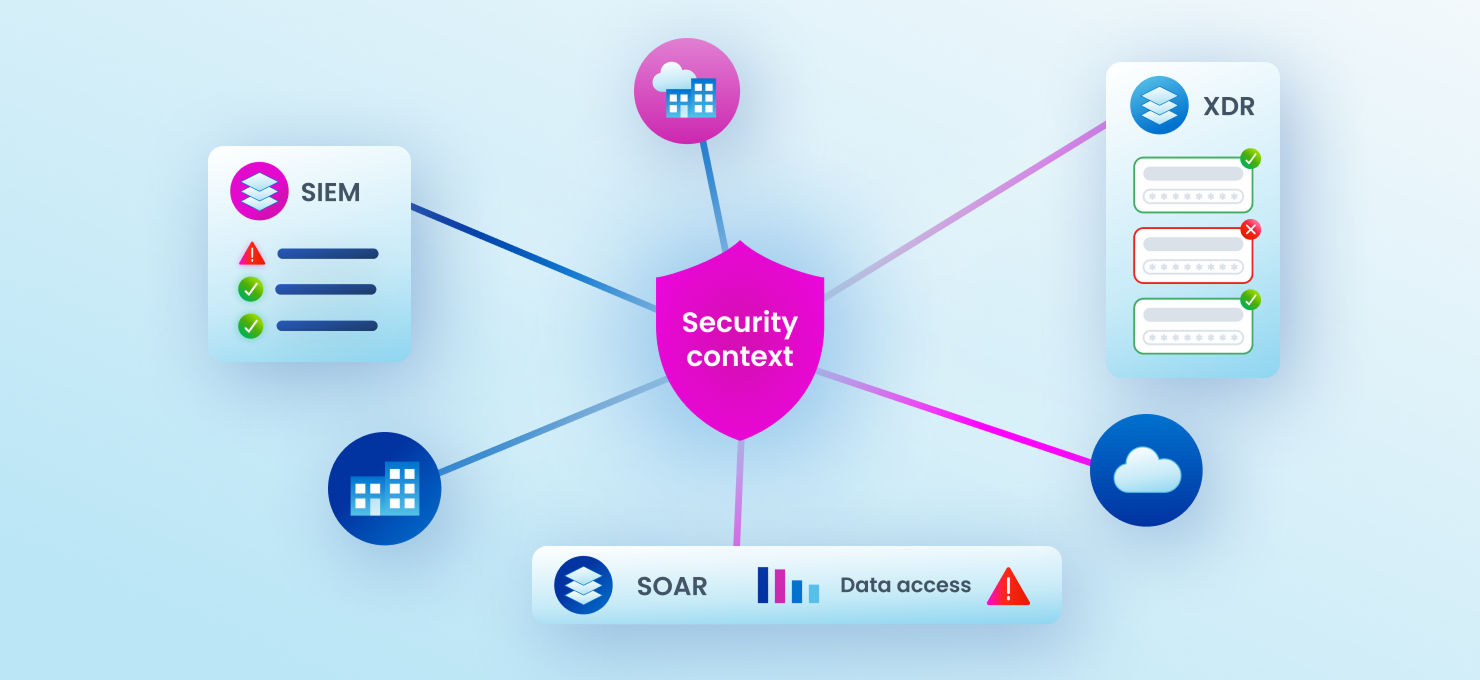
Integrate identity context with your broader security ecosystem for smarter decisions.
Prove compliance continuously with a unified view of who has access to what.
Benefits
Verify, secure, and scale with confidence
True zero trust requires more than just network controls; it requires deep identity intelligence. SailPoint enables you to operationalize zero trust principles at scale by ensuring the right people have the right access at the right time—no more, no less.
Accurate access with precision and speed
Eliminate over-provisioning by automating access rights based on roles and policies. Ensure every identity has only the access they need to do their job, reducing your attack surface without burdening IT.
Key offerings
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
Customer Stories
Success with zero trust
Leading organizations rely on SailPoint to turn zero trust principles into operational reality, securing their digital transformation.
Related resources
Optimize your identity strategy
faq
Common questions about operationalizing zero trust
What SailPoint solutions help in this area?
SailPoint offers a number of solutions designed to help you put zero trust into practice at scale. Solutions like Identity Security Cloud, Non-Employee Risk Management, and Data Access Security—all designed to automate access for all users (human, machine, and AI agents) across your hybrid environments, verify users, and give you unified control for zero trust.
How does identity security support zero trust?
Identity security is the "verify" in "never trust, always verify." It provides the central control plane to authenticate users, validate their access rights, and manage entitlements throughout the user lifecycle. Without strong identity governance, zero trust is impossible to enforce.
How does this approach handle non-human identities?
Our platform treats machine identities (bots, RPAs, service accounts) and AI agents with the same rigor as human identities. We provide visibility into machine and AI agent access, detect over-privileged accounts, and manage the lifecycle of non-human credentials to close security gaps.
What role does AI play in this solution?
AI is crucial for scalability. It analyzes vast amounts of identity and access data to detect anomalies, recommend policy changes, and automate low-risk access decisions. This allows your security team to focus on high-priority threats while maintaining a frictionless user experience.
Contact us
Adaptive identity: The foundation of enterprise security and trust
Don't let complexity stall your security goals. Empower your organization with a scalable, identity-first approach to zero trust. Protect your business, enable your workforce, and move forward with confidence.