Workflow infrastructure
Turn insight into automated action
Automate identity processes with no-code, dynamic workflows and adaptive approvals. It’s the easiest route to security and compliance confidence.
Challenge & solution
Unlock business agility with robust workflows
Manual identity workflows create bottlenecks, security gaps, and inefficiencies as organizations grow. Automate processes with dynamic workflows that adapt based on AI intelligence, risk and business context for certifications, approvals, and lifecycle events to scale security and streamline operations.
Intelligent workflows for secure identity operations
Streamline onboarding, access changes, and deprovisioning with automation.
Reduce errors with automated, consistent identity processes for enhanced security posture.
Ensure uniform enforcement of security policies across teams.
Easily manage growing identity needs with dynamic workflows that are risk and business context aware.
Automate adaptive, event-driven approvals for faster, smoother processes.
Use cases
Manage identity lifecycle
SailPoint SaaS Workflows automate identity processes, eliminating manual tasks and boosting efficiency. With dynamic workflows, quickly create, update, and replicate processes for certifications, approvals, lifecycle events, and privilege tasks. Tackle complex use cases, respond to risks, and streamline certifications to enhance security, compliance, and scalability at enterprise scale.
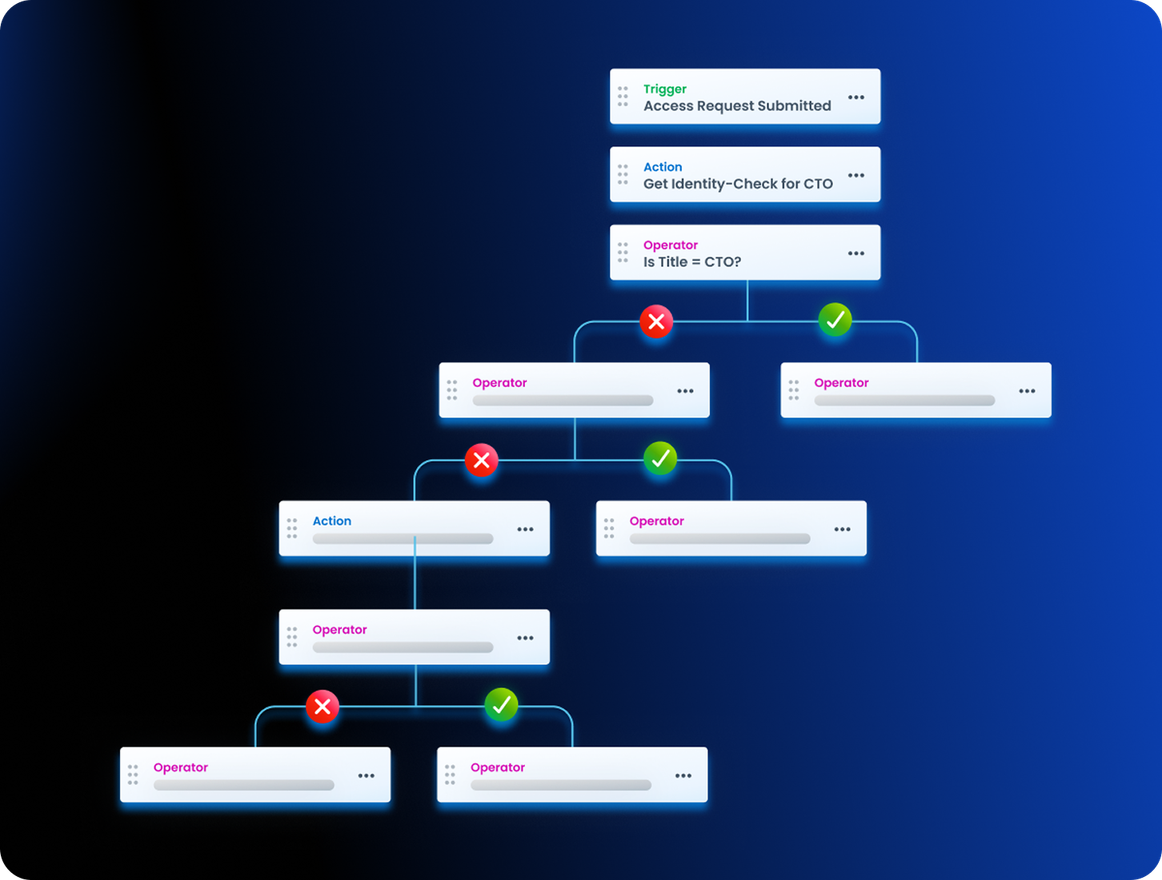
Automate the identity lifecycle
Automate the onboarding, moving or termination of any user type with dynamic workflows. Leverage adaptive approval workflows to quickly grant least privilege access to a new employee and third-party worker’s productivity. Provision and deprovision access based on lifecycle events, and business context for compliance and reduced risk.
Accelerate your risk mitigation processes
Automated workflows are available to guide you to make the right access decision with the click of a few buttons. You have the advanced logic capabilities to apply the proof you need to either keep, revoke or investigate the access further as anomalous access or threat signals are detected.
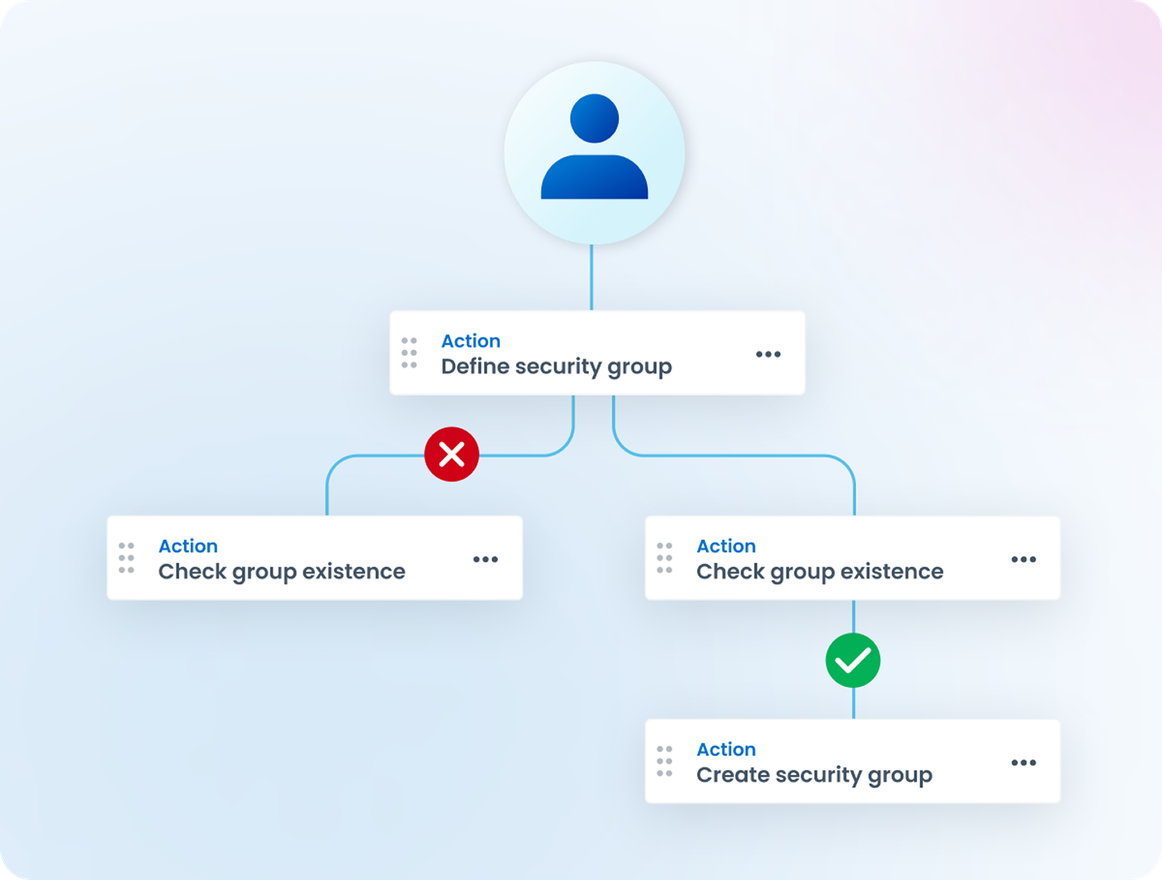
Automate Privileged Tasks
Reduce backlogs, manual work and the need for specialized knowledge when executing privileged tasks. Eliminate the need to expose credentials or initiate a privileged session. Easily build workflows and delegate privileged tasks to IT or business users with simple drag-and-drop automation.
Customer Stories
Real-world results with SailPoint workflows
Related resources
Learn how to build, automate, and optimize workflows
Start your identity security journey today
SailPoint Identity Security Cloud empowers organizations to intelligently manage and secure real-time access to critical data and applications.
Advanced capabilities
Take your identity security solution even further
SailPoint Identity Security Cloud goes beyond the basics to tackle complex identity challenges. These specialized, add-on solutions offer even greater control and intelligence for reducing risk and ensuring compliance.
faq
Frequently asked questions
Why are workflows important for identity security?
Workflows replace manual, error-prone tasks with consistent, auditable automation that reduces risk, accelerates response, and enforces least-privilege at scale.
What identity processes can be automated with SailPoint workflows?
Common use cases include joiner-mover-leaver processes, access requests and approvals, risk-based remediation, entitlement changes, policy enforcement, and certification actions.
Can workflows respond to real-time risk or security signals?
Yes. Workflows can trigger actions based on identity risk, activity changes, or external security signals to enable adaptive and automated responses.
Do workflows support just-in-time access and least privilege?
Yes. Workflows help enforce just-in-time access, remove standing privileges, and automatically revoke access when conditions change.
Can workflows use identity context and business attributes?
Yes. Workflows leverage rich identity context, including role, department, access history, risk level, and other attributes to make informed decisions.
Can workflows be reused or standardized across teams?
Yes. Organizations can create reusable workflow templates to standardize identity processes and accelerate automation.
Do workflows require scripting or coding?
No. Most workflows can be built and managed using low-code or no-code tools, making automation accessible beyond identity experts.
How do workflows support identity maturity and scale?
Workflows help organizations move from manual governance to adaptive, automated identity security that scales across all identity types.
Contact us
Put identity security at the core of securing your business






