Blog
Securing machines: The next frontier in identity security
Humans are no longer the dominant digital actors they once were. Armies of machines and workloads are now continuously communicating and making decisions at scale against an organisation's critical assets and data, without any human intervention.
These entities perform millions of machine-to-machine interactions daily, forming the digital heart of modern IT infrastructure. But while organizations often enforce strong governance over human identities, the same rigor rarely extends to non-human identities.
Each of these entities rely on a Non-Human Identity (NHI) to authenticate, connect, and operate securely. Yet most of these are typically unmanaged with weak controls. The result is an identity sprawl explosion that traditional security controls and solutions can’t handle.
NHIs remain one of the least managed aspects of enterprise security and securing them has become an urgent priority.
The current state of the industry
Gaps in traditional IAM and PAM tools
Most IAM and Privileged Access Management (PAM) platforms were built for humans, including their privileged access to machines, databases and other resources. As a result, NHIs often operate outside corporate IAM frameworks, in many cases invisible to IAM governance systems.
Managing NHIs impacts every part of an IT organization—from IAM and DevSecOps to broader cybersecurity operations. Because NHIs are provisioned, managed, secured, monitored, and retired in highly fragmented ways, traditional approaches fall short. This complexity has created the need for an entirely new generation of tools and controls designed specifically to govern the full lifecycle of machine identities.
The evolving market landscape
The good news: the industry has started to catch up.
Over the past few years, a new wave of vendors has entered the market with solutions aimed at governing non-human identities throughout their lifecycle. At the same time, established IGA and PAM providers— such as SailPoint — have expanded their offerings to address these emerging identity types. SailPoint now provides dedicated governance for non-human identities through SailPoint Machine Identity Security and AI agents through SailPoint Agent Identity Security.
Most of the solutions in the market have focused on the foundational requirements of governing and managing and securing the NHIs that exist within an organisation, in particular dealing with static, long-lived NHIs.
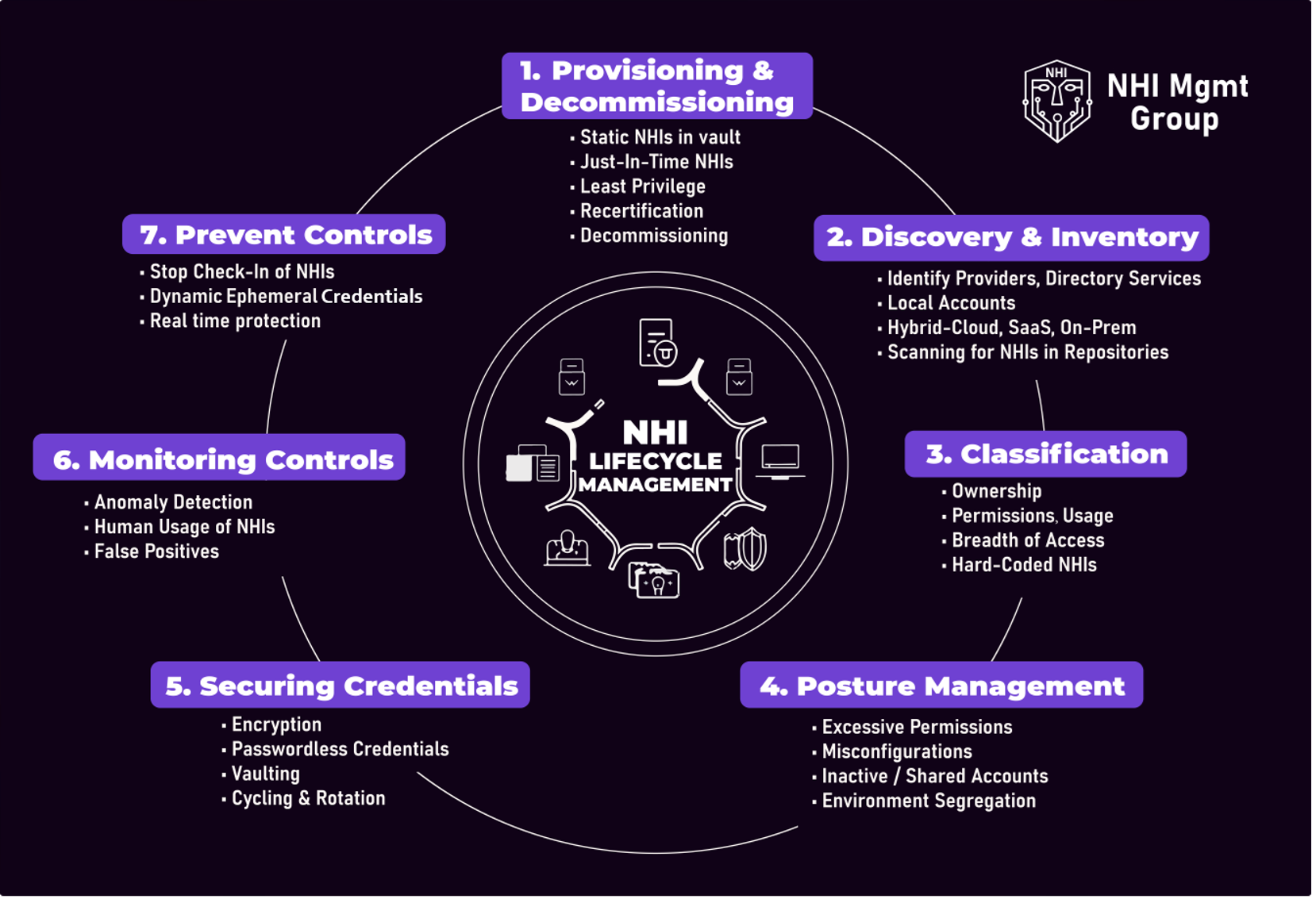
The core capabilities of these solutions include:
- Provisioning & Decommissioning – supporting core JML processes
- Discovery & Inventory – including scanning for hardcoded credentials/secrets
- Classification – ownership, permissions, usage and breadth of access
- Posture Management - excessive permissions, inactive/shared accounts, misconfigurations and environment segregation
- Securing Credentials – secrets vaults and cycling
- Monitoring Controls – anomaly detection, human use of NHIs
- Prevent Controls – stop check-in of secrets
So how does SailPoint Machine Identity Security align to these governance and lifecycle processes?
1. Convergence of human and non-human IAM
The boundary between user and workload identity will blur. Unified governance frameworks will apply consistent policies, monitoring, and risk scoring to all identities, human and non-human. Expect IGA, IAM & PAM platforms to merge functionality with ISPM and ITDR platforms.
2. AI-driven discovery and governance
AI and machine learning will play a crucial role in continuously mapping the identity landscape. By analysing inventories, source code scans, logs, cloud configurations, and network activity, AI will be able to identify orphaned or overprivileged NHIs, recommend policy adjustments and even auto-rotate credentials based on risk factors.
3. Cryptographic attestation and short-lived credentials
Static passwords and API keys are on the way out, but there is a massive legacy technology tail that still needs to be managed.
Identities will increasingly rely on short-lived, cryptographically attested tokens or certificates. Technologies like SPIFFE/SPIRE will underpin this evolution, allowing workloads to prove their identity cryptographically, not through secrets.
4. Massive growth in agentic AI systems
AI agents with adaptive reasoning and self-directed task execution will redefine the broader identity space significantly around the core concepts of impersonation, authentication, authorisation and delegation. We may need new identity protocols, cryptographic accountability frameworks and governance models capable of distinguishing, verifying, and regulating these dynamic interactions between humans, agents, workloads and data sources.
5. Regulatory pressure
Governments, regulators and standards bodies are beginning to address non-human identity explicitly, including:
- PCI-DSS version 4.0 introduces new mandates aimed at enhancing the security of NHIs.
- NIST SP 800-207 (Zero Trust Architecture) emphasizes workloads - cryptographically verifiable, tamperproof identities for users, devices, and services that grant access based on context.
- Other compliance frameworks like SOX, SOC 2, ISO 27001, and DORA are likely to expand and include NHI lifecycle control requirements.
With the rapid growth and risks of agentic AI, we can expect to see significant focus from regulators and governments on ensuring appropriate standards, controls and guardrails and identity security will be foundational to this.
The next chapter in identity security
Over the past decade, the industry has focused on securing human identities. But as automation and AI reshape enterprise operations, the next decade will centre on securing the machines and the AI agents that drive them.
It is critical as an organisation that you have a clear strategy defined around managing Non-Human Identities, especially in the era of agentic AI.
Given many organisations are likely to have huge legacy technical debt and risks with static long-lived NHIs, it will be very important to strike a fine balance between managing the existing legacy with appropriate governance controls and lifecycle processes to manage them, while you move strategically towards a zero-trust model using dynamic, ephemeral just-in-time credentials.
