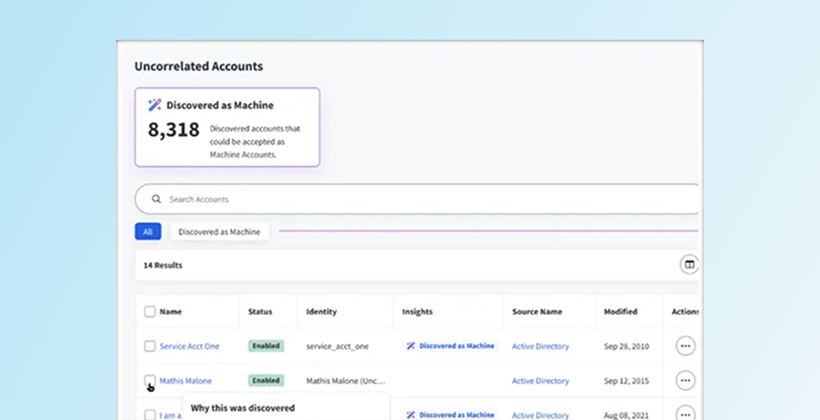
Use case
Certify machine account access
Eliminate blind spots by certifying machine account access on a recurring basis—helping to ensure compliance, accountability, and reduced risk across your environment.
Challenge & solution
Unchecked accounts, unchecked exposure
Without regular certifications, machine accounts can accumulate excessive or outdated permissions—leaving your organization exposed to potential audit findings and unnecessary risk.
Machine accounts rarely get reviewed
Certifications often focus only on human identities
Machine accounts slip through the cracks of standard IGA reviews
Orphaned accounts remain active long after they should be decommissioned
Excessive or outdated access creates audit and security risk
Certifications purpose-built for machines
Include machine accounts in recurring certification campaigns
Ensure every account is reviewed and approved by an accountable owner
Highlight high-risk or sensitive entitlements for focused review
Reduce compliance gaps with clear audit trails
Special report
Machine identity crisis: challenges & hidden risks
New research shows machine identities bring heavier workloads, audit challenges, and higher security risks. Learn why organizations struggle to govern them and what steps can close the gaps in identity management.
Benefits
Assisting to strengthen compliance and reduce risk
Certification helps ensure that machine accounts don’t escape oversight. By reviewing access on a recurring basis, you can prove compliance, eliminate orphaned accounts, and lower your exposure to security risk.
Every account under review
Bring machine accounts into certification campaigns so audits cover your full identity landscape—not just human users. Clear, documented reviews make compliance easier and reduce surprises during audits.
See SailPoint in action
Explore on your own
Take a self-guided tour of SailPoint's identity security platform
Take product tourAdvanced Capabilities
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
Related industries
Where certifications are critical
Industries with strict audit requirements need airtight certifications for every identity. Machine accounts can no longer remain an exception.
Healthcare
Certify access for accounts tied to patient systems to assist with staying compliant with privacy regulations.
Learn moreFinancial services
Ensure machine accounts in trading, payment, and reporting systems are certified to help meet audit demands.
Learn moreEducation
Regularly certify accounts tied to staff data and research systems to help safeguard compliance and accountability.
Learn moreRelated resources
Machine Identity Security resources
faq
Machine account certification: What to know
What is machine account certification?
Machine account certification is the process of regularly reviewing and validating the access rights assigned to non-human identities (NHIs) such as service accounts, bots, RPAs, and other machine accounts. Just like human access reviews, certification ensures that these accounts still serve a valid purpose and have only the permissions they need.
With Machine Identity Security, certifications are built into the governance workflow—so machine accounts aren’t treated as an afterthought. This allows organizations to enforce consistent oversight across all identities and prove that governance extends beyond just humans.
Why is certification important for machine accounts?
Without certification, machine accounts often accumulate permissions unchecked. Many are never reviewed after their creation, which means outdated or excessive access can linger for years. This creates serious compliance gaps during audits and increases the chance of unauthorized use or exploitation by attackers.
Certification establishes accountability by forcing a periodic check-in: does this account still need access? Is the level of access appropriate? Who is responsible for it? By addressing these questions regularly, organizations can reduce risk, demonstrate compliance, and ensure their identity governance program covers every corner of the environment.
How does Machine Identity Security support certifications?
Machine Identity Security integrates machine accounts directly into certification workflows that many organizations already use for human identities. Owners are prompted to review accounts under their responsibility, validate whether access is still required, and either approve or revoke permissions. High-risk or sensitive entitlements can be prioritized so that reviewers focus on what matters most. This activity is logged, providing a transparent record that helps prove governance is being applied consistently. By embedding machine accounts into the same certification cycles as human identities, governance becomes unified and scalable.
Can certifications flag high-risk access?
Yes. One of the most valuable aspects of machine account certification is the ability to highlight accounts that represent the greatest risk. This includes accounts with privileged permissions, those linked to sensitive applications, or accounts that appear orphaned without an active owner.
Machine Identity Security surfaces these accounts within certification campaigns, giving reviewers clear insight into which accounts demand extra scrutiny. This risk-based approach ensures that time is spent where it matters most—protecting critical systems and reducing the likelihood of a security incident.
How does certification align with other Machine Identity Security capabilities?
Certification complements discovery, classification, and ownership assignment. Once accounts are discovered, classified, and assigned to owners, certifications helpsensure they are continuously governed and compliant over time.
contact us
Secure and govern sensitive data access — before it’s overexposed
Discover how SailPoint can help you reduce risk, enforce least privilege, and protect sensitive data with identity-first governance.