Use case
Accelerate compliance readiness
Add data-driven insights to access certifications to streamline reviews, reduce risk, and support compliance efforts.
Challenge & solution
Traditional certifications lack data context
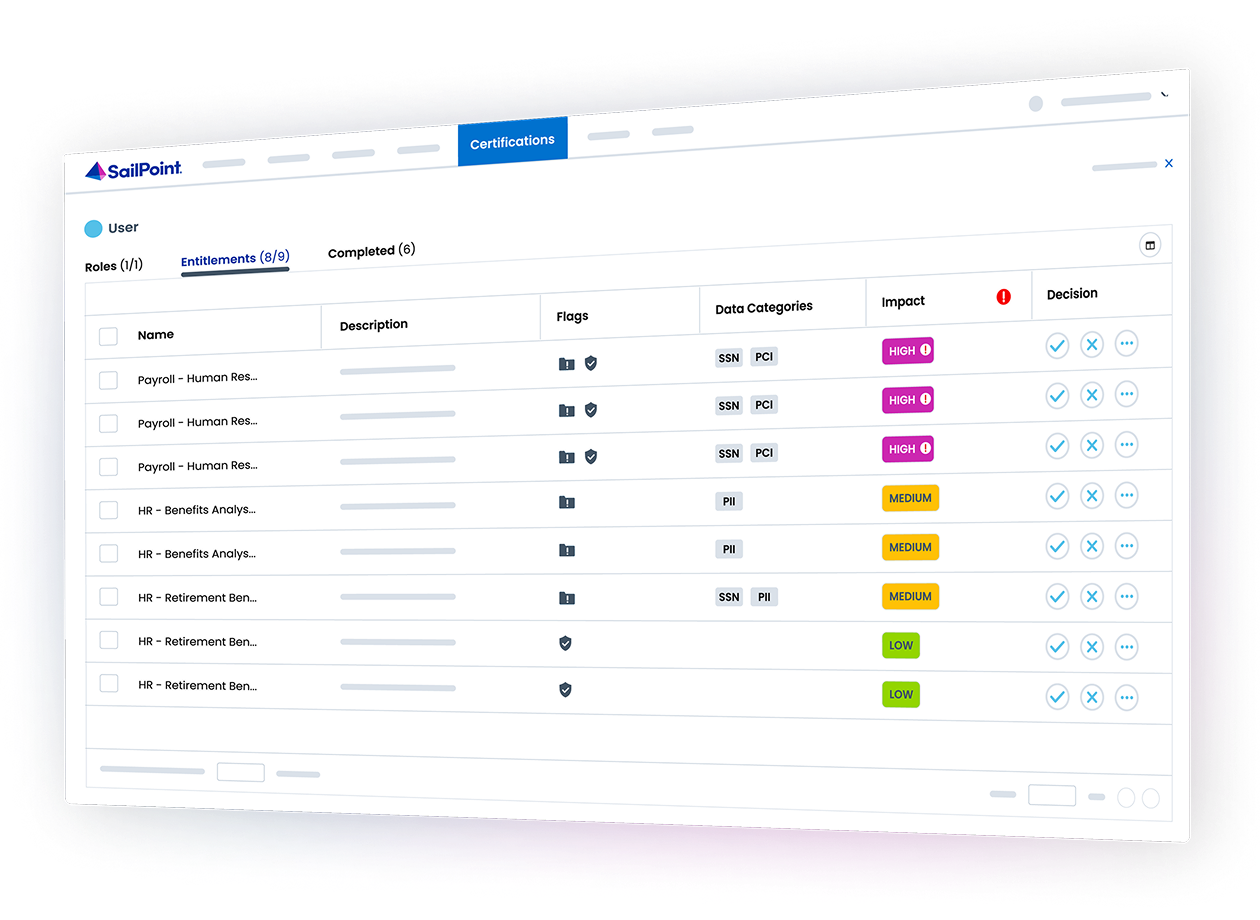
Access certifications often miss a critical layer — insight into who can access sensitive data and how that access is being used. Without visibility into data-level entitlements, reviewers are left with limited context to prioritize risk or support compliance initiatives effectively.
Enhance certifications with data access intelligence
Highlight access to sensitive, regulated, or high-risk data
Enrich access reviews with sensitivity and usage metadata
Enable focused, fine-grained certifications for data assets
Delegate review tasks to relevant data owners automatically
SOLUTION BRIEF
Data Access Security use cases
Learn how SailPoint improves identity governance by integrating data-level insight into certifications. Get practical ways to reduce review fatigue and streamline compliance readiness.
Benefits
Stronger certifications, streamlined compliance
SailPoint brings real-world data access context into your identity governance workflows — helping you focus reviews on what matters most, reduce time spent on low-risk entitlements, and strengthen your compliance processes.
Surface high-impact access in every review
Highlight user access to sensitive or regulated files, helping reviewers quickly spot potential compliance risks and make informed decisions with less effort.
Advanced capabilities
Take your identity security solution even further
SailPoint Identity Security Cloud goes beyond the basics to tackle complex identity challenges. These specialized, add-on solutions offer even greater control and intelligence for reducing risk and ensuring compliance.
See SailPoint in action
Explore on your own
Take a self-guided tour of SailPoint's identity security platform
Take product tourRelated resources
Data Access Security resources
faq
Frequently asked questions
How is SailPoint Data Access Security integrated with Identity Security Cloud?
Data Access Security is natively built on the SailPoint Platform and integrates directly with Identity Security Cloud. This provides unified visibility and governance of application, system, and data access — all from a single interface, without requiring separate tools or third-party integrations.
What are the benefits of managing data access within the SailPoint platform?
By extending identity governance and controls to data from within the SailPoint platform, organizations eliminate silos, reduce complexity, and streamline access reviews. Identity teams can apply consistent policies and controls across data without managing multiple disconnected systems.
How does Data Access Security enhance access certifications?
Without ownership, machine accounts can quickly become orphaned—meaning no one is responsible for their oversight. Orphaned accounts are a leading cause of compliance gaps and a major security risk, as they often have excessive permissions and go unmonitored. Assigning ownership establishes accountability, streamlines decision-making, and helps ensure that every account can be reviewed, certified, or decommissioned when needed.
How does Data Access Security simplify the certification process?
SailPoint can automatically delegate access reviews to appropriate data owners based on file or folder metadata. This streamlines certification workflows and improves review accuracy.
How does Data Access Security help with compliance readiness?
By providing visibility into data access, sensitivity, and usage, SailPoint helps organizations create a more efficient, transparent certification process that aligns with internal controls and regulatory expectations.
How does SailPoint ensure consistent governance across apps, systems, and data?
Because Data Access Security is integrated with SailPoint Identity Security Cloud, organizations can apply unified policies and governance controls across applications, systems, and data from a single platform. This consistency reduces policy gaps, eliminates redundant tooling, and accelerates remediation across the entire identity ecosystem.
Contact us
Put identity security at the core of securing your business