Definition of CIEM
CIEM is used to manage identities and access rights, permissions, or privileges in single-cloud and multi-cloud environments. CIEM, which stands for cloud infrastructure entitlement management, is also called cloud entitlements management or cloud permissions management. A specialized software-as-a-service (SaaS) category, CIEM provides visibility into which access entitlements are in place across cloud and multi-cloud environments.
CIEM supports a principal tenet of zero trust security, the principle of least privilege, to help organizations protect systems and data against data breaches, cyber attacks, and other vulnerabilities exposed by excessive cloud permissions. IT and security teams use CIEM to apply the principle of least privilege access to cloud infrastructure and services to minimize cloud attack surfaces by reducing the number of cloud entitlements an identity has to only the specific ones they need.
What are entitlements?
In the context of CIEM, entitlements consist of effective permissions that are assigned to users, workloads, and data. They determine what permissions a cloud identity (e.g., human users, connected devices, artificial intelligence that has access to the cloud on behalf of a human) has within cloud and multi-cloud environments and how they engage with access credentials and undergo authentication processes for privileged tasks. An entitlement is used to establish boundaries for what a cloud identity can do and which resources it can access.
What is the difference between IAM and CIEM?
Identity and access management (IAM) and cloud infrastructure entitlement management (CIEM) are two different types of cybersecurity that each address different aspects of identity and access controls. Below is a comparison of IAM and CIEM that highlights the differences.
| IAM | CIEM |
|---|---|
| IAM provides baseline access controls to manage user identities and their permissions across systems that can be either on-premises or in the cloud. Characteristics of IAM: Encompasses a broad range of functionalities, including authentication, authorization, role-based access control, and the provisioning and deprovisioning of user accounts with a focus on maintaining consistent access controls across a relatively stable set of resources and user roles. | CIEM provides capabilities that support the nuanced and flexible management needed to support cloud environments. Characteristics of CIEM: Focuses on managing and securing the rapidly changing entitlements in cloud platforms with fine-grained visibility and control over cloud permissions, detection of excessive entitlements, enforcement of least privilege policies, and automatic adjustment of permissions. |
Why cloud infrastructure entitlement management is important
Cloud providers use cloud infrastructure entitlement management to effectively and efficiently authorize identities to access resources in dynamic cloud environments and address operational, security, and compliance challenges facing cloud security personnel.
CIEM provides the ability to implement and enforce least privilege access throughout single and multi-cloud environments.
To apply and streamline management of least privilege access, cloud infrastructure entitlement management replaces existing manual processes for managing entitlements with automated processes and systems that optimize entitlements for all identities, resources, and services across all multiple cloud infrastructures and thousands of permissions, actors, and resources.
CIEM also uplevels functions, such as privileged access management (PAM) and identity governance administration (IGA), to provide the granularity required to secure access at the resource level and to scale across growing cloud environments.
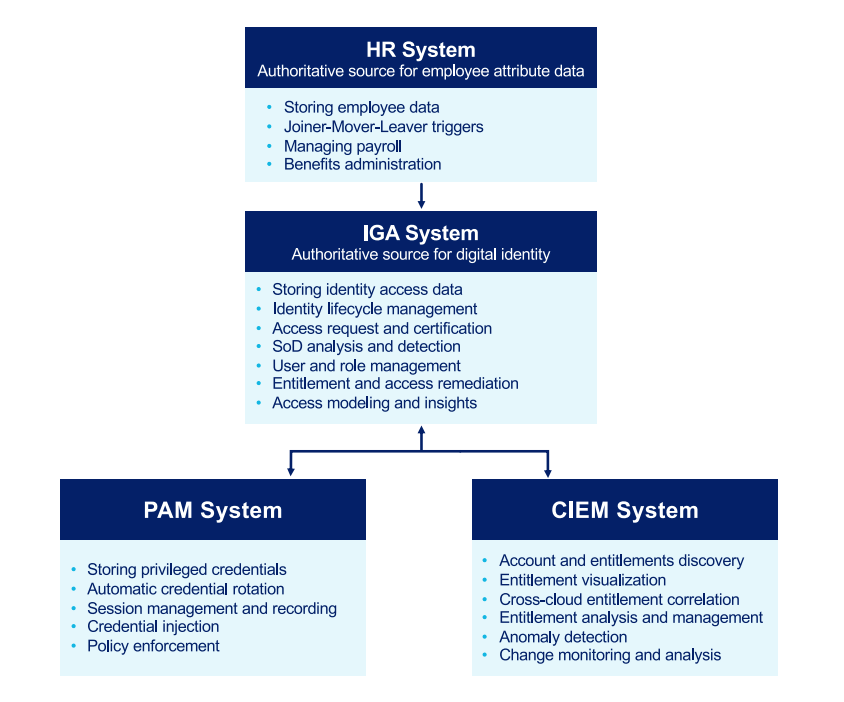
Integrating CIEM and PAM systems into the IGA system is critical in order to maintain consistent visibility and control across all points of access.
Using CIEM to implement centralized management and the concept of least privilege for these identities lowers risk across cloud environments. Cloud infrastructure entitlement management centralizes control and broad security capabilities eliminate blind spots, cloud security gaps, compliance anomalies, and vulnerabilities that can result in a breach.
Components of CIEM
The main functions of cloud infrastructure entitlement management are entitlement visibility, rightsizing permissions, advanced analytics, and compliance. CIEM solutions are comprised of different components, but all share the following three.
- Centralized management
A control center is used as a dashboard to provide centralized management for CIEM. This allows IT and security teams to efficiently use cloud infrastructure entitlement to manage single or multi-cloud environments from one place. The CIEM dashboard makes it fast and easy to monitor systems to detect anomalies and increase operational efficiencies by automating what were previously manual setting changes. - Identity governance
For CIEM, identity governance sets the entitlements that specify which apply to each cloud entity. This mitigates entitlement risk by making it easy to see the level of access granted to the cloud entities at any given time. CIEM provides visibility into cloud and multi-cloud environments using automated scanning to assess access control policies, rules, and configuration continuously and provide up-to-date details about what entitlements are in place, what each cloud entity can do based on those entitlements, and which cloud entity can access each cloud resource based on those entitlements.
After identifying an entitlement, cloud infrastructure entitlement management determines whether the access privileges a cloud entity has been granted are the least necessary for achieving their intended objectives. If the entitlement provides too much access, CIEM can alert administrators so they can address the problem manually or modify entitlements automatically, increasing efficiency in enterprise environments. - Security rules and policies
Security policies and rules determine the who, what, when, where, and why of cloud entity entitlements for accessing and controlling resources, tools, and services within a cloud or multi-cloud environment. Rather than using generic rules and conditions, CIEM access assessments are performed using powerful tools, including advanced analytics powered by machine learning and user and user entity behavior analytics (UEBA). CIEM rules and policies consist of and govern:
- Security protocols in security information and event management (SIEM) provide details about the highest level of workload access a user should be able to obtain at any given time.
- Metric logging in SIEM tracks usage to identify entitlements with signs of misuse to prioritize least-privilege access and prevent vulnerabilities due to over-privileging.
- Compliance management and certification in SIEM automate assessments by continuously comparing existing entitlements to security regulations and requirements to ensure compliance. Cloud infrastructure entitlement management can also detect instances where configuration changes have made entitlements that were once compliant come out of compliance.
How cloud infrastructure entitlement management is used
Cloud infrastructure entitlement management is used to take cloud access management beyond identifying human users’ privileges. Because non-humans commonly access cloud instances, CIEM also manages cloud entitlements for applications, machines, and service accounts as well as connected devices that need access to applications and databases, such as IoT (Internet of Things) devices (e.g., printers, surveillance cameras, card readers) and OT (operational technology) devices (e.g., sensors, robots, programmable logic controllers or PLCs).
CIEM also enables the enforcement of granular access controls that restrict access and prevent unsanctioned data sharing. This is vital in cloud and multi-cloud environments that can have millions of individual entitlements to manage.
CIEM brings the power of automation to ensure that entitlements are tightly managed and least-access controls are enforced as requirements continually change.
CIEM can also recommend the least privileges for a particular type of work, using advanced techniques such as machine learning.
An example of how cloud infrastructure entitlement management can be utilized is when a user requests access to a system to verify a configuration. The user can be granted temporary, one-time access to perform the task. Once the job has been completed, access can be automatically revoked. An audit will show exactly what permissions the user had at any given time. This can be used to track down malicious behavior or supply machine learning data sets to help improve least-privilege access recommendations.
CIEM and cloud security
Cloud infrastructure entitlement management was born out of necessity. As cloud computing continued to present increased complexity and security vulnerabilities, organizations looked for a better way to manage entitlements in cloud and multi-cloud environments.
CIEM was created for cloud and multi-cloud environments to secure and manage the thousands of applications, services, and users accessing cloud resources. CIEM makes managing privileges, access rights, and identities more effective and efficient by continuously assessing and validating the privileges and access rights of identities accessing cloud resources, following the tenets of zero trust security.
In addition, CIEM dashboards provide a central location for managing entitlements and mitigate risks related to mismanaged entitlements of users. Access automation services available through CIEM supports the deployment and scaling of cloud and multi-cloud ecosystems.
How does CIEM improve cloud security?
As organizations expand their cloud infrastructures, managing access becomes increasingly complex and cumbersome due to the sheer volume of identities and permissions involved. By integrating CIEM into cloud security architectures, organizations can not only strengthen their defense mechanisms but also manage security at scale more strategically. The following are several core capabilities of CIEM solutions that facilitate the efficient management of these environments at scale to improve cloud security.
Automated management of entitlements
CIEM solutions improve cloud security by providing automated tools to manage and adjust entitlements in real time. As cloud environments evolve, CIEM solutions can continuously assess and modify permissions to align with changing conditions—without human intervention. This dynamic approach prevents privilege creep and ensures that outdated or unnecessary permissions are decommissioned in a timely manner.
Compliance assurance
By helping organizations meet regulatory requirements regarding data protection and access controls, CIEM ensures that cloud security systems align with best practices. This includes providing mechanisms to enforce consistent policies across all cloud services. In some cases, compliance functionality is automated within the CIEM, such as generating audit trails and reports to identify areas that need to be updated or improved.
Enforcement of least privilege access
Enforcing least privilege access is another way that CIEM solutions improve security across cloud environments. Abiding by the principle of least privilege ensures that users, applications, and systems are granted only the minimum level of access necessary to perform their jobs. By restricting access rights, CIEM reduces the risk of accidental or malicious security incidents that can result from overprivileged accounts.
Scalability and multi-cloud protection
With the widespread growth of multi-cloud environments, managing security across different cloud platforms is increasingly difficult. CIEM solutions are built to scale and work across different cloud providers, offering unified security capabilities that simplify security operations and management in complex, multi-cloud environments.
Visibility and control
CIEM tools improve cloud security by offering comprehensive visibility into all cloud resources and their associated permissions. This allows security teams to identify and fix misconfigurations and improperly assigned or excessive permissions. Enhanced visibility also helps security teams better understand and control how, when, and by whom cloud resources are accessed.
Benefits of cloud infrastructure entitlement management
Key benefits of CIEM at a glance
- Secures cloud ecosystems at scale with protections against access point vulnerabilities
- Analyze the entitlements landscape to expose risk and detect threats
- Automates all monitoring processes
- Gives comprehensive visibility into all entitlements and their use among organizations’ users, non-human identities, and cloud resources
- Keeps individual users within the parameters of their access roles
- Makes it faster and easier for organizations to implement and maintain least-privilege access controls for all
- Manages access consistently and appropriately across all cloud resources
- Monitors identities across different cloud environments and ensures that they meet defined governance requirements
- Provides audits of existing privileged accounts and entitlements
- Remediates vulnerabilities related to excessive access privileges
- Revokes access privileges and eliminates credentials from cloud entities no longer associated with an organization
- Designed for easy integration with existing security solutions and different cloud solutions
Key CIEM benefits
Overall, cloud infrastructure entitlement management fills the gaps in organizations’ cloud security and provides many benefits in a centralized way for cloud and multi-cloud deployments. The list above summarizes CIEM benefits; following are details about some specific CIEM benefits.
Automation
With CIEM, rules can be put into place to trigger automatic actions for specified situations, such as using it to enforce security policies. Examples include enforcing multi-factor authentication (MFA) requirements or limiting permissions to users based on their role.
Improved compliance
CIEM ensures the integrity and validity of cloud entities’ entitlements through continuous monitoring, alerts, and remediation. With the automation and consolidation of cloud entities’ access management systems across cloud and multi-cloud platforms, these environments maintain compliance and are audit ready.
Cross-cloud correlation and insights
By aggregating data about cloud entities across the enterprise’s entire cloud deployment, cloud infrastructure entitlement management makes it easier to enforce access control policies consistently. This also enables CIEM to provide a unified audit trail across all cloud and multi-cloud environments.
In addition, CIEM can analyze this data for trends that can be a sign of malicious activity. This data can also be used to define groups for similar users and identify cases where separation of duties and least privilege access should be employed.
Continuous, granular visibility
Cloud infrastructure entitlement management provides continuous, granular visibility into organizations’ cloud infrastructure along with details of all the permissions and activity within the cloud or multi-cloud environment. This enables teams to see who is accessing what cloud resources and when by enabling more effective monitoring and management of access controls.
Improved security posture
A well-designed and implemented CIEM solution provides enhanced security protections by:
- Reducing the attack surface
- Assessing and prioritizing issues and recommending remediation tactics
- Creating and maintaining an accurate inventory of all existing entitlements
- Detecting anomalous cloud transactions that may be a sign of threats, such as malicious activity, human error, or violations of security protocols
- Enforcing the principle of least privilege, a key tenet of zero trust security
- Identifying and automatically updating entitlements that are misconfigured, unused, or in violation of policy
Rightsized permissions
Cloud infrastructure entitlement management makes it easy to rightsize permissions to prevent IT and security teams from applying broader permissions than necessary to save time. With CIEM, it is simple to provision individual resources based on specific access requirements and adjust privileges as needs change.
Risk reduction and enhanced security
CIEM allows for the implementation of zero trust in an organization’s security by implementing the principle of least privilege. Zero trust is a cybersecurity approach where implicit trust among users is eliminated by validating every stage of digital interactions. This, coupled with the fact that CIEM allows for continuous monitoring of how permissions are being used, reduces risk to a cloud environment, thus enhancing its security.
Speed and agility for DevSecOps
CIEM helps DevSecOps teams manage access configuration for cloud infrastructure with the granular permissioning necessary to maintain least privileged access, allowing them to accelerate rollouts or provision services without compromising security.
Visibility from a single dashboard
A CIEM dashboard provides a centralized overview of entitlements across multiple cloud platforms, making it easier to control access and privileges, which results in improved identity management. This view of entitlements also supports risk assessment and remediation strategies.
Selecting a CIEM solution
A common question when the topic of cloud infrastructure entitlement management solutions arises is, “Do we really need one?” Here few instances that can guide the decision.
| When a CIEM should be added | When a CIEM addition can be delayed |
|---|---|
| A sandbox environment is needed for development and testing work. All identities in the cloud environment require continuous monitoring (even if there are only a few). Automated identity management is required. Compliance is a priority, and the landscape is complex. There are a large number of cloud entities in the environment. | The cloud environment does not have many cloud entities. The cloud environment is private and closed. |
| When a CIEM should be added | When a CIEM addition can be delayed |
|---|---|
| A sandbox environment is needed for development and testing work. All identities in the cloud environment require continuous monitoring (even if there are only a few). Automated identity management is required. Compliance is a priority, and the landscape is complex. There are a large number of cloud entities in the environment. | The cloud environment does not have many cloud entities. The cloud environment is private and closed. |
When selecting a CIEM solution, evaluate these features and functions:
- Ability to integrate the current architecture and security stack
- Automated detection, remediation, and mitigation capabilities
- Capabilities to analyze all policy types and security posture
- Comprehensive visibility
- Cross-cloud correlation
- Discovery of every cloud entity and account activity
- Entitlement optimization and protection
- Implementation guidance
- Logging and reporting capabilities for compliance and other audits
- Reliable cloud support
- Support for federated and native identities
- User-friendly interface
CIEM FAQ
Below are answers to some frequently asked questions about cloud infrastructure entitlement management.
How do you pronounce CIEM?
Rather than a simple verbalization of each letter, CIEM is commonly pronounced as a single word, “kim.” Using this pronunciation streamlines and provides clarity in verbal communication related to CIEM solutions and deployments.
Why is CIEM important?
CIEM is purpose-built to support least privilege access controls, which enhances the security of cloud ecosystems and facilitates adherence to compliance requirements in the complex and dynamic environments of cloud-based infrastructures. By implementing least privilege access, CIEM solutions effectively minimize the attack surface. In addition, its focus on granular, dynamic access control not only bolsters security but also supports compliance efforts, making it an important part of cloud security strategies.
What challenges in entitlement management are addressed with CIEM?
Compliance and regulatory requirements
Most organizations must adhere to strict regulatory requirements for data access and privacy. CIEM solutions automate the enforcement of access policies to help organizations effectively and efficiently follow regulatory standards. It also provides audit trails and detailed reports to demonstrate compliance during audits.
Identification and mitigation of risks
Complex multi-cloud environments make it difficult to gain a clear view of which users have access to what resources, making the identification of potential security risks challenging. CIEM solutions address this by providing granular visibility into entitlements and usage patterns. This enables organizations to detect and mitigate risks such as unused permissions, abnormal access behaviors, and potential insider threats.
Multi-cloud environment management
When services from multiple cloud providers are used, which is common for many organizations, managing entitlements across these diverse platforms can be exceedingly difficult. CIEM solutions provide support as cloud deployments are scaled to support higher usage volumes in multi-cloud environments.
Over-provisioning of permissions
CIEM solutions address the over-provisioning of permissions, which is one of the most common issues in cloud environments. This is when users or entities have more access rights than necessary for their roles—in direct contradiction to the principle of least privilege. These excess entitlements create security vulnerabilities that can lead to data breaches. CIEM systems enforce the principle of least privilege to restrict entitlements and minimize attack surfaces.
Rapid changes in cloud environments
Cloud infrastructures are inherently in flux, with resources being added, modified, or removed as requirements change. Traditional entitlement management systems often struggle to keep pace with these changes. CIEM solutions address this by providing automated tools that can dynamically adjust permissions in real time based on predefined policies and real-time analysis, ensuring alignment with security protocols.
Visibility and control over entitlements
As cloud ecosystems grow, maintaining visibility and control over who has access to what becomes increasingly difficult, leaving sensitive data at risk of being compromised. CIEM solutions provide comprehensive visibility into all entitlements across cloud platforms.
What is the difference between CSPM vs. CIEM?
| CSPM (cloud security posture management) | CIEM |
|---|---|
| Focuses on identifying and managing risks related to cloud resource configurations by: -Continuously monitoring cloud environments to detect misconfigurations, compliance violations, and potential security gaps -Automating the process of reviewing and remediating settings across cloud services according to best practices and regulatory standards -Providing visibility into the cloud architecture -Alerting security teams to misconfigurations (e.g., unsecured data storage options or improperly configured network access controls) | Focuses specifically on managing and securing user permissions and entitlements within cloud environments by: -Enforcing the principle of least privilege -Providing detailed insights into who has access to what resources -Helping security teams control and manage access rights effectively -Reducing permission sprawl -Mitigating the risks of insider threats or accidental data exposure due to excessive permissions -Automates the detection and remediation of improper permission settings |
Together, CSPM and CIEM provide a comprehensive approach to cloud security that addresses the configuration of the cloud environment and the management of identities and entitlements within it. This layered approach to cloud security ensures that organizations can leverage cloud technologies safely and efficiently with a robust defense against potential threats and vulnerabilities.
Cloud infrastructure entitlement management for today’s enterprise security portfolio
With the unceasing move to cloud environments, organizations must pay more attention to cloud security. Legacy solutions have limitations in today’s enterprise environment. The ability of CIEM to meet the stringent security requirements that the enterprise demands, combined with their ability to scale at pace with new deployments, have made CIEM attractive to many organizations.
