Use case
Govern and secure sensitive data
Uncover, govern, and remediate risky access to sensitive enterprise data – all as part of an identity-first security strategy.
Challenge & solution
Stop data overexposure before it becomes a breach
Uncontrolled data access is a growing risk — with excessive permissions, shared files, and ungoverned accounts leaving sensitive information exposed. Security and IT teams need visibility into how enterprise data is accessed, used, and shared across users, systems, and AI tools.
Extend governance to data access
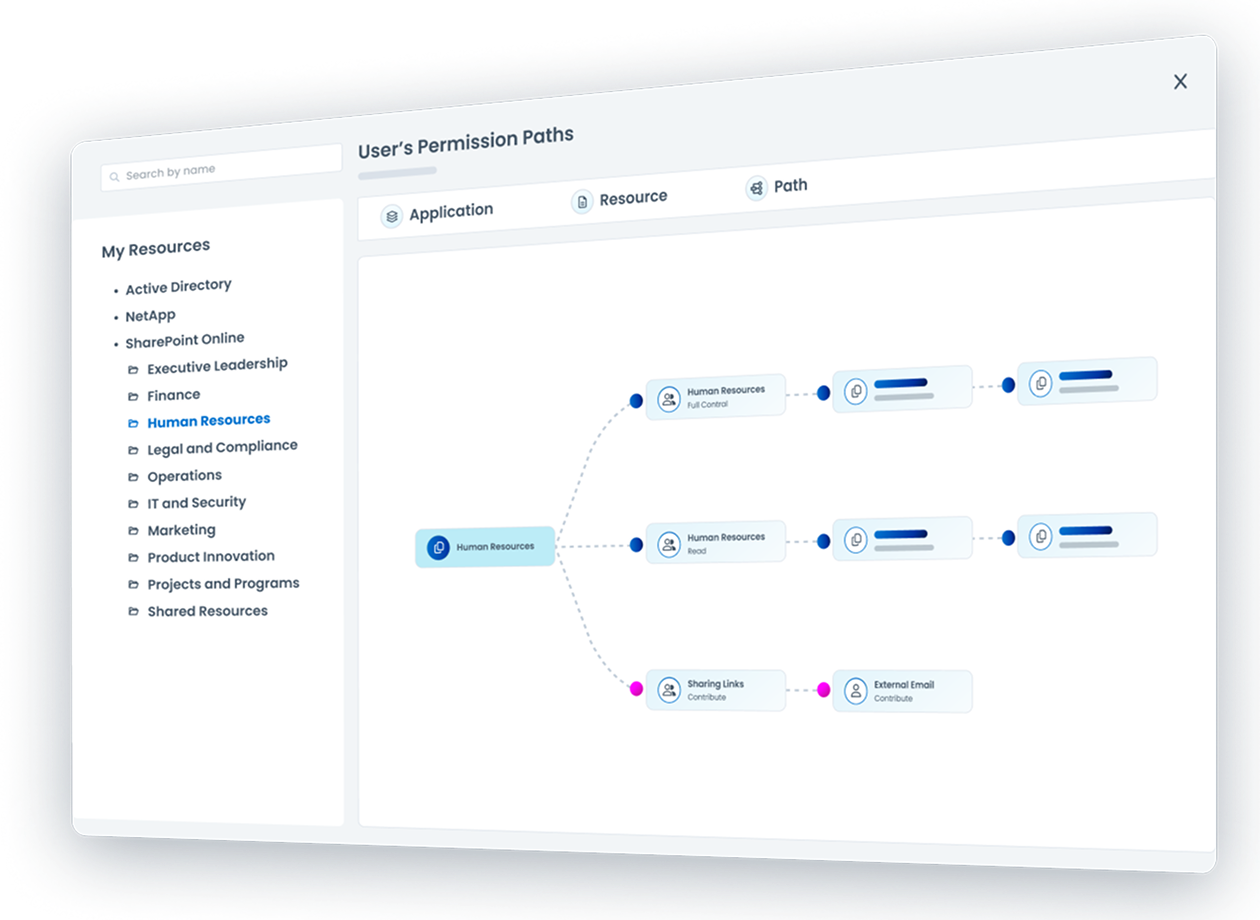
Discover overexposed or externally shared sensitive data
Identify over-privileged users, including non-employees
Target orphaned, dormant, or misconfigured accounts for governance
Assist with dynamic data governance based on least privilege
SOLUTION BRIEF
Data Access Security use cases
See how SailPoint helps organizations reduce risky data access, enforce least privilege, and protect sensitive information. Explore key use cases and capabilities in this solution brief.
Benefits
Smarter data access governance, built for modern risk
SailPoint Data Access Security helps you identify and enable the remediation of risky data access across users, systems, and AI tools. From detecting over-permissioned access to managing unauthorized sharing, you gain proactive control over who can access your data — and how.
Proactively detect over-privileged identities
Uncover identities with unnecessary or elevated permissions to sensitive data — and right-size access based on actual need, reducing the risk of insider threats or lateral movement.
See SailPoint in action
Explore on your own
Take a self-guided tour of SailPoint's identity security platform
Take product tourAdvanced Capabilities
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
Related industries
Data Access Security by industry
Explore how SailPoint helps industry leaders govern access to sensitive data, meet compliance requirements, and reduce risk.
Financial services
Govern access to financial data to help protect against insider threats and regulatory fines.
Learn moreGovernment
Help protect citizen data by controlling sensitive access across federal, state, and local agencies.
Learn moreManufacturing
Help Safeguard proprietary designs by controlling access to operational and supplier data.
Learn moreRelated resources
Data Access Security resources
faq
SailPoint Data Access Security FAQ
How does SailPoint Data Access Security help identify over-privileged access to sensitive data?
SailPoint Data Access Security analyzes access permissions across data repositories to detect when users have more access than required. It highlights excessive privileges — including full control or edit access to sensitive content — and helps organizations enforce least-privilege access models.
Can SailPoint Data Access Security detect broadly or externally shared sensitive data?
Yes. SailPoint identifies sensitive data that is exposed via open shares, “Everyone” groups, anonymous links, or to users outside the organization. These findings are prioritized for review to reduce risk and exposure.
Does SailPoint Data Access Security help remove dormant or misconfigured accounts with access to data?
Yes. SailPoint detects stale or orphaned accounts that still retain access to data repositories. It flags these accounts so that administrators can remove or remediate unnecessary access and reduce attack surfaces.
Can SailPoint Data Access Security enforce least-privilege access policies?
Yes. SailPoint helps organizations enable policy-driven access controls that enforce least-privilege by aligning data access with role, sensitivity level, and usage context. This helps organizations reduce unnecessary entitlements and improve security posture.
How does SailPoint Data Access Security assist with unauthorized data sharing prevention?
By detecting abnormal or high-risk sharing patterns — such as external link creation or inappropriate permissions — SailPoint alerts administrators and enables corrective actions like revoking access or initiating reviews.
Does SailPoint Data Access Security help with compliance and audit requirements?
Yes. SailPoint Data Access Security provides detailed access visibility and activity monitoring that supports compliance with regulatory mandates. It helps streamline audits by offering clear ownership, access logs, and automated reporting on sensitive data access.It assists users to align their data classification with compliance frameworks like GDPR, HIPAA and SOX, supporting ongoing compliance readiness.
contact us
Secure and govern sensitive data access — before it’s overexposed
Discover how SailPoint can help you reduce risk, enforce least privilege, and protect sensitive data with identity-first governance.