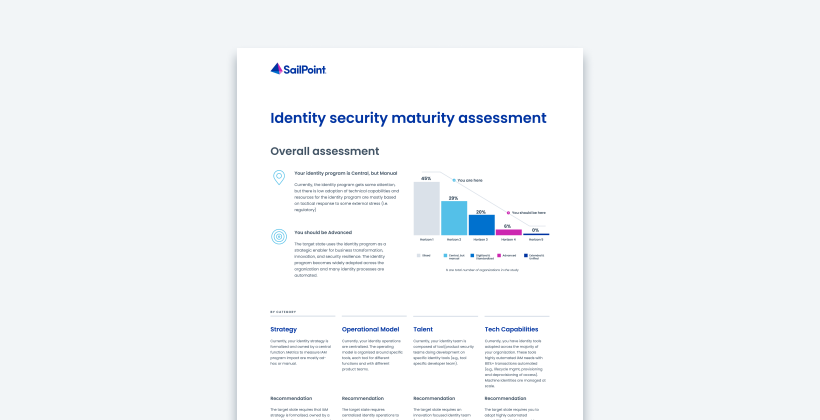
healthcare
Accelerate healthcare identity management
Reduce IT burden and increase efficiencies within your hospital or healthcare identity management program through AI-driven identity security.

Overview
Modernize your healthcare identity security program
Hospitals and healthcare organizations are struggling to quickly enable their staff while securing against targeted cyber attacks.
Organizations need to find ways to reduce their risk and simplify meeting complex compliance requirements. Healthcare identity management is no small task and cannot be handled through manual processes. Healthcare is uniquely challenged with securing individuals with one-to-many roles with multiple authoritative sources within complex user populations.
However, healthcare organizations can increase their security posture and gain operational efficiencies through AI-driven identity security.
Assign only the right level of access
Prevent friction between clinicians and IT security staff
Reduce IT burden managing manual tasks
Govern third-party non-employees and machine identities
Simplify audit readiness and easily demonstrate compliance
Blog
SailPoint named Best in KLAS 2025 in identity management
A Best in KLAS award signifies to the healthcare IT industry the commitment and partnership that the top vendors should provide.
Imprivata partnership
SailPoint and Imprivata unified identity security
SailPoint and Imprivata have an alliance to help benefit healthcare organizations worldwide with an integration of our best-of-breed identity security and access management solutions. Learn how to safeguard and automate access to your healthcare organization’s most critical applications and data without sacrificing clinical efficiency.
Learn moreBenefits
Quickly & securely grant access
Rapidly provision access
Securely enable clinicians and staff to be productive from Day 1.
Reduce IT burden & increase efficiencies
Reduce the strain on IT by automating manual processes. Efficiently onboard and offboard staff through automation and machine learning.
Govern non-employee access
Track affiliated physicians, travel nurses and other users' access and activity. Govern the right level of access for the right amount of time.
Reduce risk & demonstrate strong identity security controls
Ensure Zero Trust with least privileged access. Protect sensitive ePHI data and prevent disruption to patient care. SailPoint’s platform affords you the flexibility to align to various frameworks such as NIST and HITRUST and easily meet regulatory requirements such as HIPAA, GDPR, and others.
Simplify audit readiness
Replace manual processes and the cost of compliance by automatically generating audit trails and access reports on all key applications and data.
Seamlessly connect your EHR & other applications
Integrate EHR, credentialing, HR, ERP, learning management, and other applications to accomplish an identity security ecosystem.
Accelerate your digital transformation
Accommodate an expanding organization, M&A (Mergers and Acquisitions), or shifts to the cloud by confidently managing and governing all digital identities, accounts, assigned entitlements, and applications.
INTEGRATIONS
Seamlessly connect to healthcare applications
Create a more secure environment for health records and alleviate highly manual and complex EHR provisioning efforts.
Epic
Learn how to automate Epic EMP (Employees) and Epic SER (Schedulable Epic Resource) provisioning.
More about EpicCerner
Allow consistent enforcement of access and corporate compliance policies across Cerner EHR.
More about CernerMEDITECH
Provide deep integration to govern identities with management of Accounts and Roles.
More about MEDITECHCustomer Stories
Leading companies count on SailPoint for identity security
Resources
Expand your identity security expertise
Suites
Start your identity security journey today
SailPoint Identity Security Cloud enables organization to manage and secure real-time access to critical data and applications for every enterprise identity with an intelligent and unified approach.
Compare suitesFAQ
Healthcare frequently asked questions
Identity security can be complex and knowing where to start can be a challenge when you’re investing in a product or solution. We’re here to help. Find answers to common questions below.
What is Healthcare Identity Security?
Identity Security for healthcare is the discovery, management, and governance of employee and non-employee entitlements and data access.
What applications does SailPoint connect to and support?
SailPoint has connectors and integrations to hundreds of different applications and IT resources.
How does Identity Security align to Zero Trust?
Because Zero Trust relies on the identity of the user, securing identities and making sure access is appropriate all the time is critical.
What is HHS 405(d)?
HHS 405(d) is a publication that was produced to provide the health care sector an initial blueprint on ways to cost effectively help mitigate cybersecurity risks within small, medium and large organizations. It contains a targeted set of applicable & voluntary guidance. Learn more here
What is HITRUST?
The HITRUST Approach is built upon the comprehensive and scalable HITRUST CSF framework, which helps organizations of all sizes implement and enhance information risk management and compliance programs. Learn more here
References
The State of Identity Security 2023: A Spotlight on Healthcare
DISCLAIMER: THE INFORMATION CONTAINED IN THIS WEBPAGE IS FOR INFORMATIONAL PURPOSES ONLY, AND NOTHING CONVEYED IN THIS WEBPAGE IS INTENDED TO CONSTITUTE ANY FORM OF LEGAL ADVICE. SAILPOINT CANNOT GIVE SUCH ADVICE AND RECOMMENDS THAT YOU CONTACT LEGAL COUNSEL REGARDING APPLICABLE LEGAL ISSUES.
Get started
See what SailPoint identity security can do for your healthcare organization
Discover how our solutions enable healthcare organizations to meet the challenge of ensuring secure access to resources without compromising productivity or innovation.
Members of leading healthcare organizations