Blog
Unlock smarter governance with automated data ownership election
Find the right data owners for your organization’s sensitive information
How do you know who should have access to sensitive data if your organization struggles to identify who owns it in the first place? Well, it’s hard. In fact, it’s nearly impossible to secure access to business-critical information when you don’t first know who owns that data.
This is why we built SailPoint’s new automated data ownership election capability into our Data Access Security solution — to empower security teams to automatically identify data owners and more effectively govern access to critical data.
These innovations lead to faster and smarter access decisions by those who know the data best – enabling a more scalable approach to identity security.
Why is finding the right data owners so hard?
Data ownership is a moving target
In large enterprises, data is routinely created, manipulated, and shared by many different teams across various departments, so understanding its lineage can be hard. Who originally created a document—marketing, sales, engineering, customer support—might not be the same team or individual that edited it and saved it on SharePoint or Google Drive.
This data lineage is often blurred by employees who join or leave an organization – or even shift roles across departments, leading to orphaned data that often goes unnoticed and unmanaged.
Data is spread across modern and legacy systems
Large organizations evolve over time. As a result, they often have decades of accumulated knowledge distributed across legacy systems, various shared drives, and older databases. These systems don’t always have clear metadata. They might not even be tied to any team or business unit – or they might be duplicated or inconsistent across systems.
M&A activity complicates an already complicated process
When companies scale or undergo mergers and acquisitions, systems may get mashed together without a focus on unified governance. Data gets siloed. Your IT team is already overburdened, and they may be struggling to identify and assign data owners based on limited knowledge and time. M&A activity only complicates this often-tedious process.
Fast access to data is prioritized over secure access
Quick access to data sometimes wins out over security. It’s not uncommon to discover that an entire team has gained access to a set of sensitive data after being granted access to an entire folder to speed up the access required to complete a project. Over time, this leads to sprawling, unmanaged access permissions, making it difficult to tell who should have access to that data versus who does have access to it.
The value of identifying data owners
The users at the core of managing access to data are the data owners. They are closest to the data in question and understand its importance to the business, which enables them to help make better decisions on who should have access to data – and who shouldn’t.
Without data owners, the time and effort of deciding who should have access, managing access request, and monitoring access falls to IT and security teams. This often leads to delayed access to critical data and overburdened security teams. When IT teams are swamped with a barrage of these types of data access requests, they are spending less time on other critical activities, like implementing new processes to harden your overall security posture.
How SailPoint helps solve these data security challenges
Data Access Security extends your identity security program by identifying sensitive, regulated, and critical data assets within your environment. Building on this foundation, our new automated data ownership election capability helps your security teams proactively determine data owners and delegate the responsibilities of governing access to the users that own the data.
With Data Access Security, identity security teams can:
- Save time identifying and assigning data owners
- Delegate governance decisions to the people closest to the data
- Expedite better-informed governance and data access decisions
- Reduce the risks of over permissive data access
- Accelerate secure access to critical information
How it works
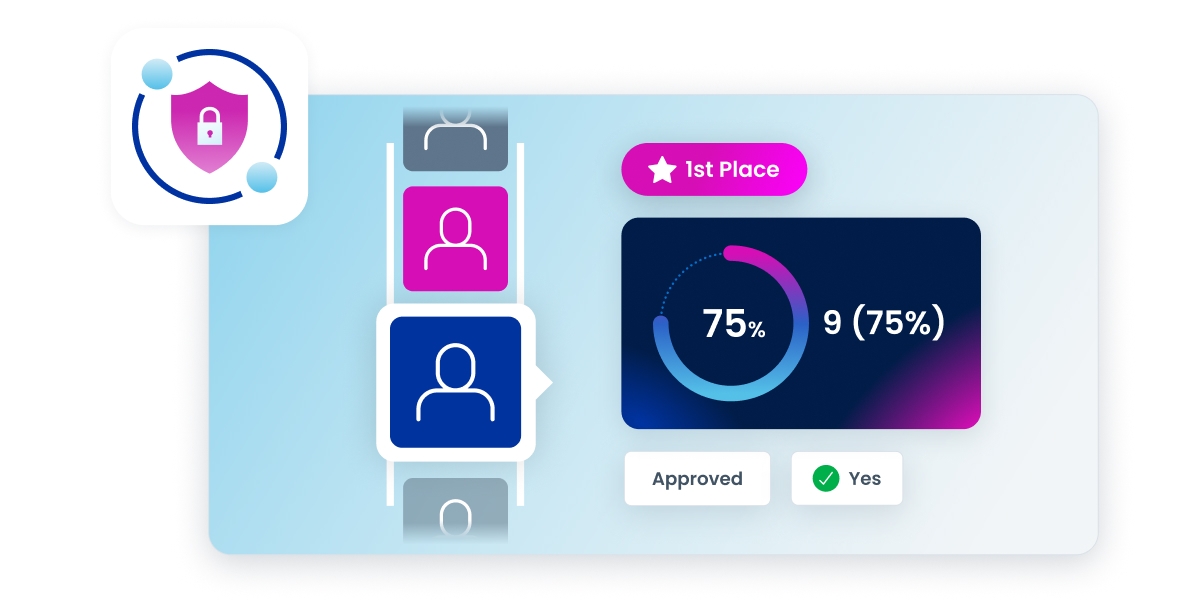
Our unique approach to data ownership election helps admins identify potential data owners from among the most likely business users using targeted campaigns.
First, campaigns are used to identify data owner candidates from among business stakeholders based on their activity and interaction with the data in question.
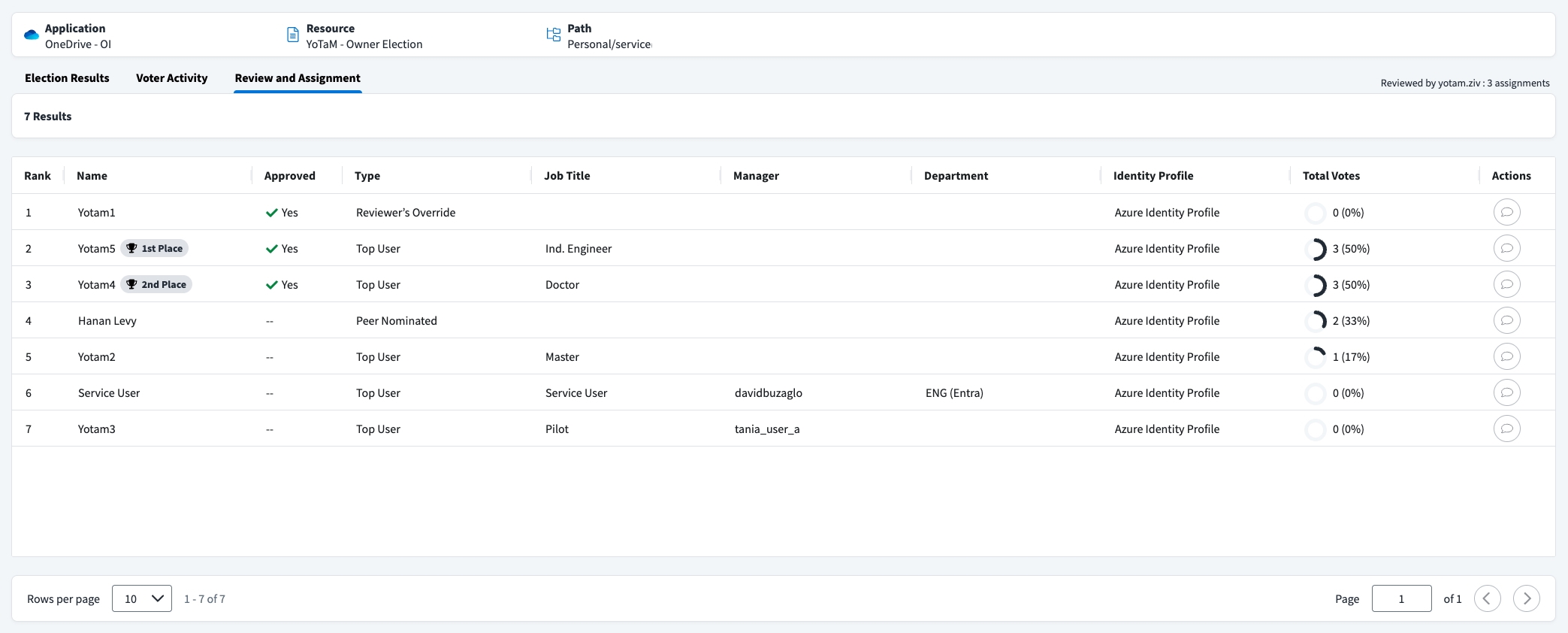
Data Access Security then analyzes activity data and recommends potential ownership candidates, as well as automatically sets the audience to participate in the collaborative, crowd-sourced voting campaigns to elect and assign owners.
Election results can be reviewed by designated reviewers before being automatically or manually assigned to the data assets themselves. Once assigned, Data Owners receive a notification inviting them to assume their governance responsibilities in Data Access Security, and they can be natively incorporated into governance processes as reviewers in access certifications, recipients of security alerts, and more.
By automating the identification and assignment of data owners, Data Access Security helps organizations adopt a more delegated approach to governance that expedites governance decisions, enables more informed decisions, and reduces governance and administration overhead from small, overburdened IT and IGA teams.
Empowering identity security teams to take control of data
Your organization creates and manages mountains of data spread across various file storage systems and sharing tools – and everyone wants (and needs) access right away. Breaking down silos and ensuring you have the right data owners helps identity security teams accelerate safe access to your information. The result is safe and efficient access to data to help your teams thrive.
With improved data access governance, your sensitive assets stay secure, your access policies are aligned, and you can continue to accelerate compliance readiness and sustainability.
Check out our latest eBook or get a customized demo to see how to secure sensitive data as an integral part of your identity security strategy.
DISCLAIMER: THE INFORMATION CONTAINED IN THIS ARTICLE IS FOR INFORMATIONAL PURPOSES ONLY, AND NOTHING CONVEYED IN THIS ARTICLE IS INTENDED TO CONSTITUTE ANY FORM OF LEGAL ADVICE. SAILPOINT CANNOT GIVE SUCH ADVICE AND RECOMMENDS THAT YOU CONTACT LEGAL COUNSEL REGARDING APPLICABLE LEGAL ISSUES.
