Security for non-human identities
Govern the identities you can’t see
Gain complete visibility and control over the fast-growing world of machine accounts, bots, and AI agents
Challenge & solution
Uncover your biggest identity blind spot
Your environment is filled with non-human identities—service accounts, bots, and AI agents that automate critical tasks. But these identities often operate without clear ownership or oversight. Created outside of standard processes, they become invisible, over-permissioned, and unmanaged, creating significant cyber security gaps that attackers are eager to exploit.
Bring your identities into the light
Discover every identity: Automatically find and classify non-human identities across your entire technology stack.
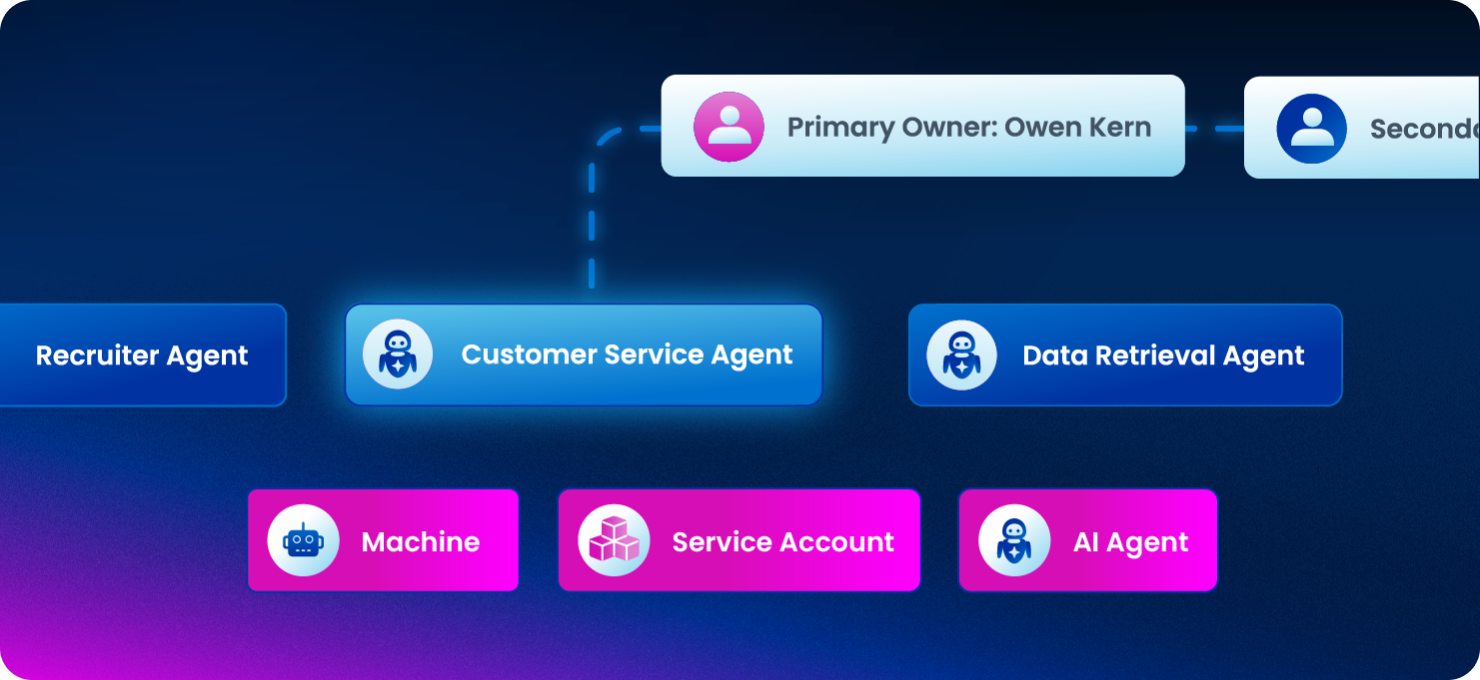
Establish clear ownership: Assign every bot, service account, and AI agent to a human owner for accountability.
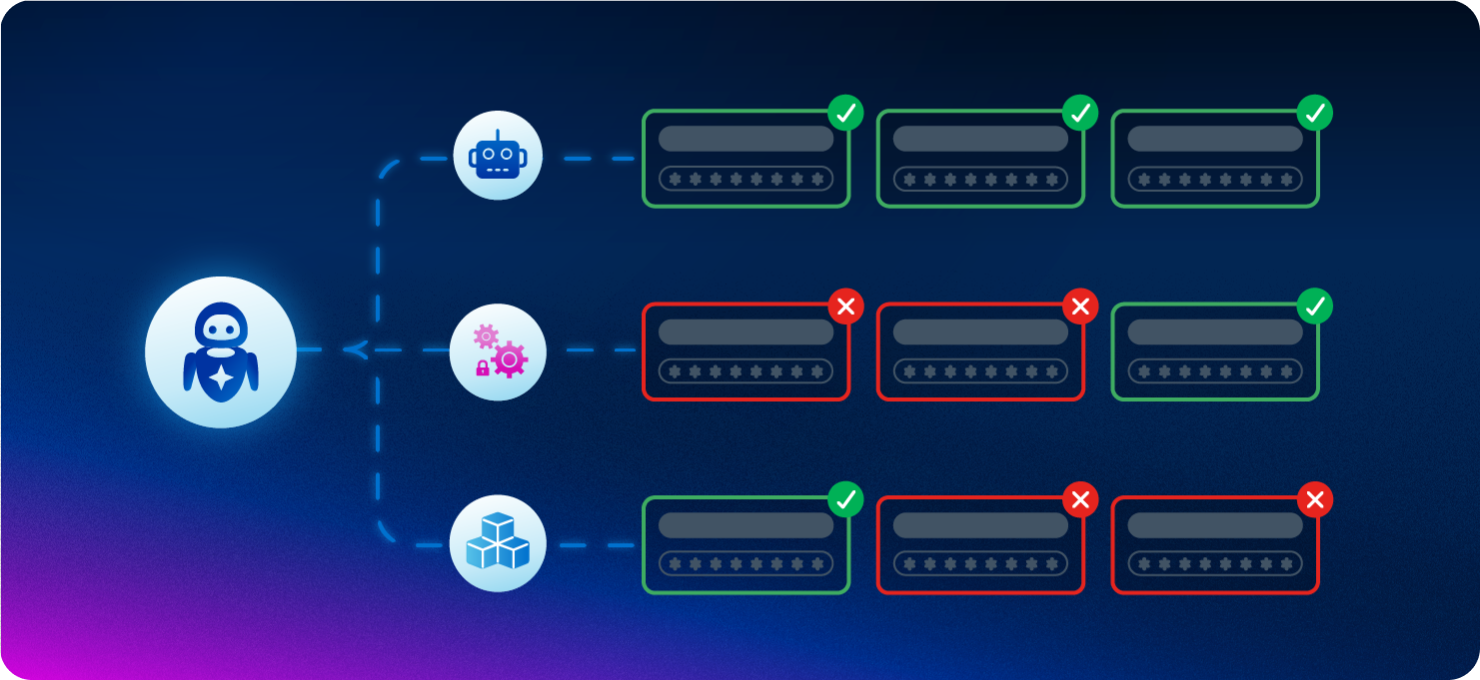
Govern the full lifecycle: Manage identities from creation to retirement with automated policies and controls.
Reduce your attack surface: Eliminate orphaned accounts and excessive permissions to close dangerous security gaps.
Strengthen compliance: Bring non-human identities into your access review and audit processes seamlessly.
Benefits
See and secure every identity
Take control of the non-human identities that power your business. SailPoint provides an adaptive, unified approach to discover, manage, and secure every service account, bot, and AI agent. This gives you the confidence that every identity—human and non-human—is accounted for and secure.
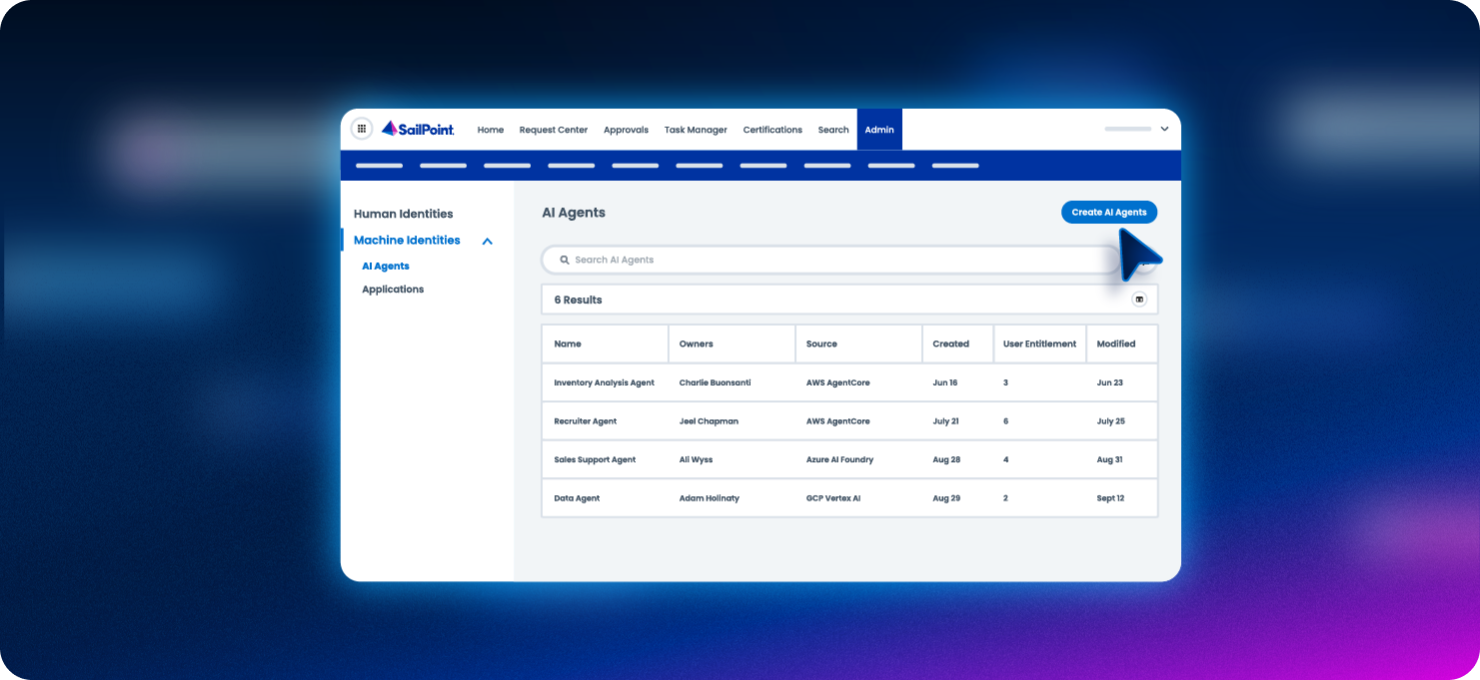
Find and take action on every non-human identity
You can’t protect what you can’t see. Automatically discover and catalogue non-human identities wherever they exist, eliminating blind spots and creating a centralised, authoritative inventory. From there, take action to reduce cyber risk, close security gaps, and ensure every non-human identity is properly governed.
Key offerings
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
Related resources
Optimise your identity strategy
faq
Answers for your non-human identity questions
What is a non-human identity?
A non-human identity represents an entity like a service account, bot, Robotic Process Automation (RPA), or AI agent that requires access to perform automated tasks. These identities are essential for business operations but lack the built-in lifecycle and ownership of human identities, making them a unique security challenge.
Why are non-human identities a security risk?
They are often created outside of formal processes, granted broad permissions, and forgotten over time, creating a hidden attack surface. Attackers target these “unowned” accounts to gain access, escalate privileges, and move through an organisation’s network undetected.
How is governing an AI agent different from a standard bot or service account?
While all are non-human, AI agents introduce new complexities. They can act autonomously, make decisions, and interact with data in non-deterministic ways. Governing them requires understanding their unique behaviours, the tools they use, and ensuring they operate within secure, predefined boundaries.
How does SailPoint establish ownership for an identity that has no human user?
Our platform allows you to assign one or multiple human owners—such as an application owner or a team lead—to every non-human identity. This creates a clear line of accountability for access approvals and periodic reviews, ensuring no identity is left unmanaged. Built-in succession planning ensures ownership can transition seamlessly when roles change, so no non-human identity is ever left unmanaged.
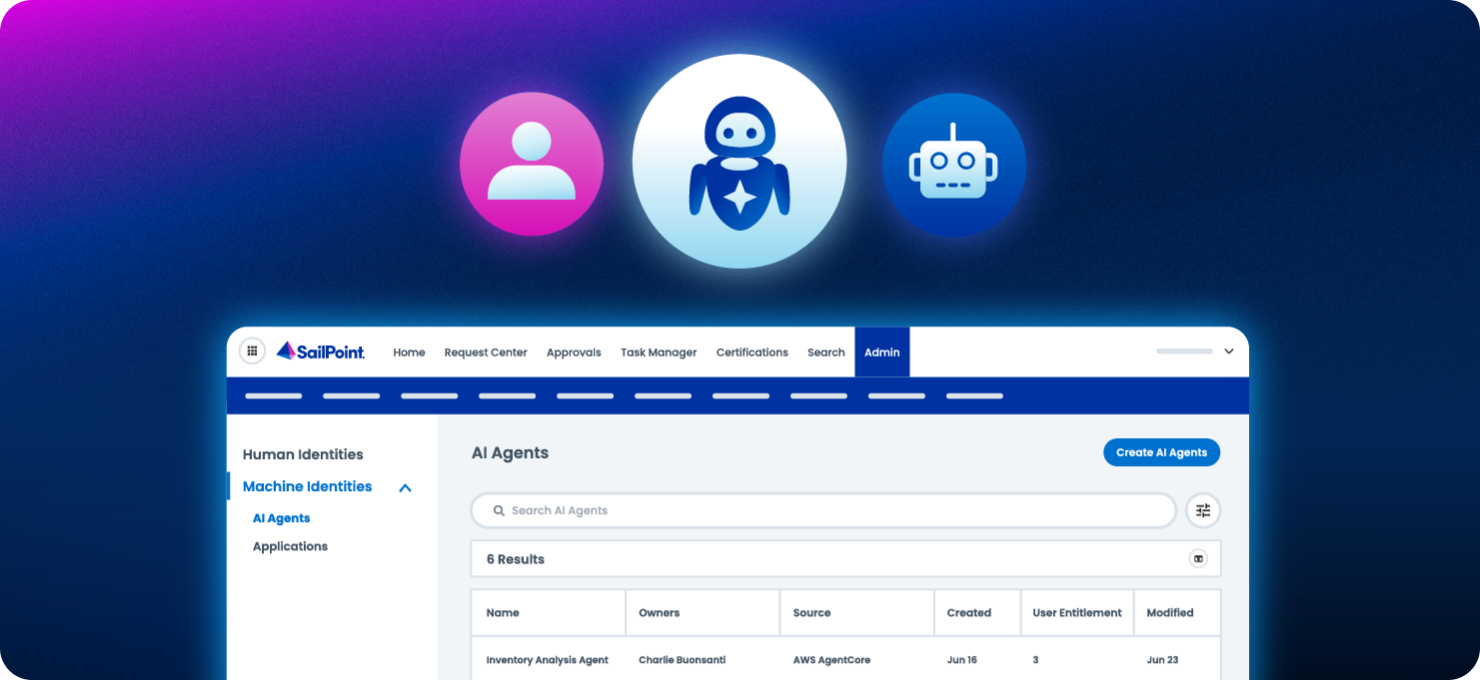
Can I manage both my human and non-human identities in one place?
Yes. SailPoint Identity Security Cloud governs human, non-employee, machine, and agent identities within one unified experience. This enables consistent policy enforcement, streamlined access certifications, a complete view of access risk across your entire organisation for humans and machines alike, and allows for complete lifecycle control through a single governance platform. This unified approach reduces complexity, closes security gaps, and simplifies compliance across all identity types.
How does non-human identity governance support compliance?
Non-human identity governance supports compliance by providing visibility, accountability, and auditability for automated access. By maintaining a centralised inventory of non-human identities, assigning clear human ownership, and tracking access changes over time, organisations can demonstrate control over how systems and processes access sensitive resources. Regular access reviews and documented lifecycle actions create an auditable trail that helps satisfy regulatory requirements and reduces friction during audits.
contact us
Secure identities hiding in plain sight
Discover how a unified, adaptive approach to identity security can help you govern every bot, service account, and AI agent with the same confidence as your human workforce.