The identity security journey
Authored by Jaishree Subramania, Vice President of Product Marketing
In my last blog, we looked at the four major elements defining the future of identity security – derived from our 2022 Horizons of Identity Security research study. While it may take some time to reach different aspects of this future, we do know that all companies are on a journey to get there – even though some may not know it yet.
To understand the current identity landscape, we evaluated companies on four key vectors in the study. We found that companies going through an identity security journey to achieve this future vision fall across 5 distinct horizons. Today I’ll expound a bit on the enablers (aka vectors) and the different Horizons.
The Four Key Enablers
An organization’s position across the horizons is determined by its maturity in each of four areas:
- Strategy
- Technology & tools
- Operating model
- Talent
Responses to each enabler help us understand how organizations reach new horizons. An identity strategy aligned with business goals can accelerate technology transformation and innovation. Identity capabilities, technologies, and tools are more efficient if they are automated and integrated with security operations. A central and strategic operating model should span across an organization, with well-defined success metrics tracked and communicated. People are crucially important, of course. An effective IAM workforce is focused on product innovation and automation rather than helpdesk responses.
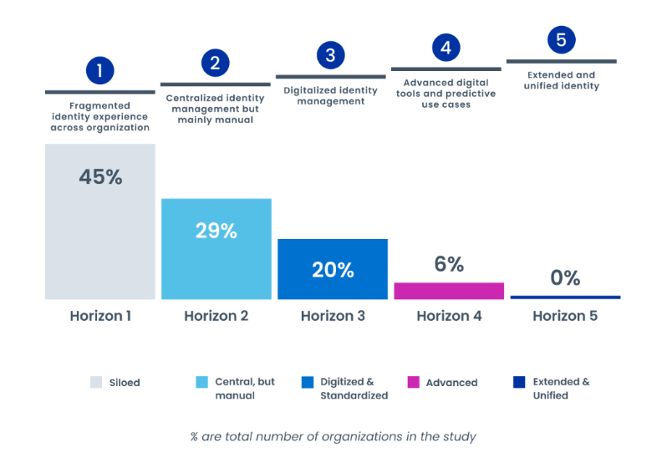
The Five Horizons
- At Horizon 1, organizations lack an identity strategy, operating model, and capabilities needed to develop a solution. It’s the least advanced.
- At Horizon 2, organizations have launched an identity management program–but it is mostly manual. They may have started to purchase tools, but there is low adoption and buy-in.
- At Horizon 3, the identity program has become digitalized, scaled up, and more widely adopted across the organization. A centralized operating model is organized around capabilities tied to specific tools, and this tool-centric engineering drives implementation and maintenance.
- At Horizon 4, organizations are using advanced digital tools and predictive technology. The identity program becomes a strategic enabler for business transformation, innovation, and security resilience. It is highly automated; AI drives decisions based on risk estimates.
- Horizon 5 is closest to the future of identity – serving as a critical control point in reducing cybersecurity risk and supporting businesses in next-gen technology innovation. The IAM strategy is a pillar of broader innovation for the organization.
Find out where you are on your journey today with our quick 6-question assessment. Upon completion, you’ll receive a customized report showing where you are in your journey and what your next best step is to realize the essential benefits of an advanced identity program, along with the full Horizons of Identity Security Report.
This report fully validates what we’ve seen among our customers, especially in the last few years – we’ve achieved an average ROI of 69% per year, all while lowering overall risk posture. Even in your core business, where else could you find a return like that? Identity security has evolved to be core to not only securing the enterprise today but enabling rapid digital and organizational transformation and innovation. From that lens, wouldn’t you want to strive for the best, aiming for horizons 4 and 5?



Discussion